Alternate format: Cyber threat bulletin: Impact of COVID-19 on cyber threats to the health sector (PDF, 724 KB)
About this document
Audience
This Cyber Threat Bulletin is intended for the cyber security community. Subject to standard copyright rules, TLP:WHITE information may be distributed without restriction. For more information on the Traffic Light Protocol, see https://www.first.org/tlp/.
Contact
For follow up questions or issues please contact the Canadian Centre for Cyber Security at contact@cyber.gc.ca.
Assessment base and methodology
The key judgements in this assessment rely on reporting from multiples sources, both classified and unclassified. The judgements are based on the Canadian Centre for Cyber Security’s (CCCS) knowledge and expertise in cyber security. Defending the Government of Canada’s information systems provides the Cyber Centre with a unique perspective to observe trends in the cyber threat environment, which also informs our assessments. CSE’s foreign intelligence mandate provides us with valuable insight into adversary behavior in cyberspace. While we must always protect classified sources and methods, we provide the reader with as much justification as possible for our judgements.
Our key judgements are based on an analytical process that includes evaluating the quality of available information, exploring alternative explanations, mitigating biases and using probabilistic language. We use terms such as “we assess” or “we judge” to convey an analytic assessment. We use qualifiers such as “possibly”, “likely”, and “very likely” to convey probability.
The contents of this document are based on information available as of 1 June 2020.
Estimative language
The chart below matches estimative language with approximate percentages. These percentages are not derived via statistical analysis, but are based on logic, available information, prior judgements, and methods that increase the accuracy of estimates.
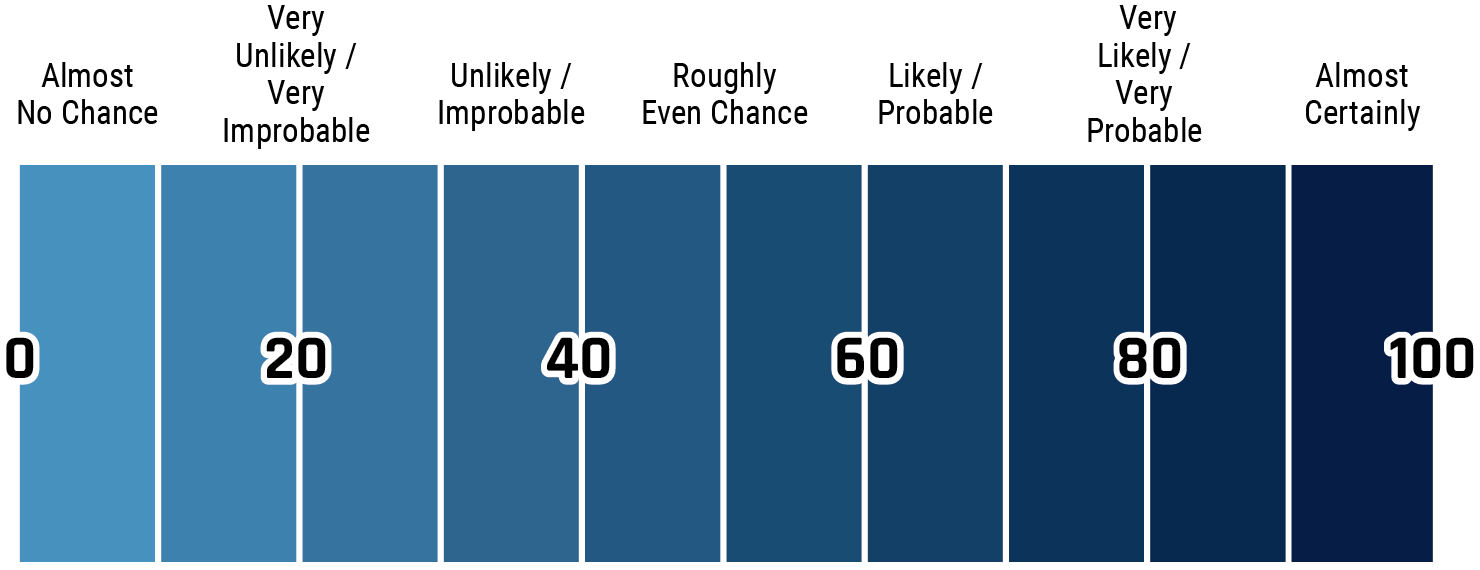
Long description - Estimative language
- Almost no change – 0%
- Very unlikely/very improbable – 20%
- Unlikely/improbable – 40%
- Roughly even chance – 50%
- Likely/probably – 60%
- Very likely/very probable – 80%
- Almost certainly – 100%
Key Judgements
- We assess that national and international public health organizations will almost certainly continue to be targeted by cyber threat activity such as ransomware, information and credential theft, and distributed denial of service (DDoS) attacks.
- We assess that cyber threat actors will almost certainly continue to target hospitals, medical clinics, and other front-line services involved in COVID-19 responses around the world. While there have been many ransomware attacks against hospitals abroad, the Cyber Centre has not been engaged to provide assistance related to a major ransomware event against a Canadian hospital during the pandemic as incidents were likely localized and managed by hospital cybersecurity teams. However, we assess that Canadian hospitals are very likely to be as attractive to threat actors as other hospitals, particularly if they are at the centre of a local outbreak.
- We assess that foreign intelligence agencies will almost certainly continue to use their cyber capabilities to pursue intelligence related to COVID-19 medical research and intellectual property. Intellectual property, especially related to vaccine development, treatments, COVID-19 testing, and medical devices such as ventilators or personal protective equipment (PPE), would offer public health, economic, and national security benefits.
- We judge that online influence campaigns will almost certainly continue to spread falsehoods and foment greater skepticism of official statistics and statements regarding the COVID-19 pandemic.
- Although we do not assess that Canada is a high priority target for online influence activities, that could change quickly, especially in response to increased political tensions with some states. In addition, many Canadian allies are a target for online influence campaigns and their information ecosystems are closely intertwined with that of Canada.
- We judge that pandemic response efforts will almost certainly continue to be negatively impacted by online fraud activity related to COVID-19, which diverts resources from legitimate responses and distributes counterfeit and substandard goods.
COVID-19-related targeting of the health sector
On 11 March 2020, the World Health Organization (WHO) officially declared the novel coronavirus disease 2019 (COVID-19) a global pandemic. In a previous Cyber Threat Bulletin, we assessed that cyber threat actors have taken advantage of this context to conduct a range of cyber threat activities.Footnote 4 The health sector—which we define as including public health institutions, hospitals and other front-line medical providers, research organizations, and pharmaceutical and medical equipment companies—is being targeted by both cyber criminals and state-sponsored cyber threat actors. The Cyber Centre assesses that in Canada and many other countries health sector organizations almost certainly face increased threats to their cyber security due to the COVID-19 pandemic.Footnote 5
Remote work introduces vulnerabilities
Health sector organizations face an increasing threat surface as employees shift to remote work arrangements.Footnote 1 In March 2020, Microsoft found several dozen hospitals with vulnerable remote work infrastructure, such as gateway appliances and virtual private networks (VPNs).Footnote 2 The Cyber Centre has issued alerts regarding vulnerabilities in remote work software provided by companies such as Citrix, Fortinet, Palo Alto, and Pulse that are being actively targeted by cyber criminals and state-sponsored actors.Footnote 3
Public health institutions
We assess that national and international public health organizations will almost certainly continue to be targeted by cyber threat activity such as ransomware, information and credential theft, and distributed denial of service (DDoS) attacks. State-sponsored actors are interested in the information related to pandemic responses held by national and international public health institutions. Cyber criminals recognize that these institutions are under pressure to continuously coordinate response efforts and provide information to the public and therefore have a high willingness to pay for the restoration of their systems. In late-March, threat actors sent COVID-19-themed malicious emails attempting to deliver ransomware to a Canadian government health organization engaged in pandemic response.Footnote 6 Earlier in March, the WHO’s chief information security officer stated that the organization had experienced an increase in cyber threat activity during the COVID-19 pandemic.Footnote 7 Malicious emails sent to the WHO attempted to gather credentials, which could then have been used to access sensitive information or to target additional victims.
When cyber criminals successfully conduct ransomware and DDoS attacks against public health institutions, they can disrupt efforts to slow the spread of COVID-19 by hampering information dissemination and coordination. For example, a DDoS attack against a Dutch government website temporarily took down the webpage that provided COVID-19 information to the public.Footnote 8 DDoS attacks can be used as a means of extortion by cyber criminals, and state-sponsored actors may use DDoS attacks as part of an online influence campaign to embarrass their targets or remove legitimate sources of information.
Front-line medical providers
We assess that cyber threat actors will almost certainly continue to target hospitals, medical clinics, and other front-line services involved in COVID-19 responses around the world. Although several ransomware operators promised to refrain from targeting front-line medical providers during the pandemic,Footnote 10 between March and April 2020, hospitals and healthcare centres in the Czech Republic,Footnote 11 the US,Footnote 12 Spain,Footnote 13 and GermanyFootnote 14 were targeted in ransomware attacks. While there have been many ransomware attacks against hospitals abroad, the Cyber Centre has not been engaged to provide assistance related to a major ransomware event against a Canadian hospital during the pandemic, as incidents were likely localized and managed by hospital cybersecurity teams. However, we assess that Canadian hospitals are very likely to be as attractive to threat actors as other hospitals, particularly if they are at the centre of a local outbreak. One ransomware campaign targeted eleven front-line healthcare providers in the US.Footnote 15 Brno University Hospital, a facility that conducts COVID-19 testing in the Czech Republic, had to disconnect hospital systems as a result of a cyber intrusion on 11 March, and hospital operations were disrupted.Footnote 16 A medical centre in Colorado was forced to use paper and manual records on 21 April due to a ransomware attack.Footnote 17
Vulnerabilities from medical devices
Hospitals and other healthcare providers face unique cyber security challenges stemming from the diverse medical devices connected to their networks, especially medical Internet of Things (IoT) devices. According to a survey released in March 2020 by Palo Alto Networks, 83% of medical imaging devices in the United States are running unsupported operating systems.Footnote 9 Cyber threat actors can use unpatched devices or legacy systems to compromise hospital networks and steal data or undertake a ransomware attack.
Front-line medical providers are popular ransomware targets because they have significant financial resources and network downtime can have life-threatening consequences for patients. Cybercriminals view this as good odds for a substantial ransom payment. Beyond immediate disruptions, organizations hit by ransomware may also face data breaches, a threat used by many ransomware operators to coerce victims into paying. Since November 2019, the Cyber Centre has observed multiple ransomware campaigns exfiltrate and leak victim data after ransom payments were refused. This is a serious threat for front-line medical providers who possess sensitive personal health information that would have legal and reputational consequences if leaked.
Intellectual property and supply chains
We assess that foreign intelligence agencies will almost certainly continue to use their cyber capabilities to pursue intelligence related to COVID-19 medical research and intellectual property. Given the unexpected spread and severity of the disease, governments almost certainly feel they are operating with inadequate information to craft effective public health and economic responses to the COVID-19 pandemic. As such, foreign intelligence agencies are almost certainly being tasked with new intelligence collection requirements related to the COVID-19 pandemic. It is also likely that cybercriminals affiliated with affected governments are targeting the health sector to supplement official intelligence collection efforts. Intellectual property, especially related to vaccine development, treatments, COVID-19 testing, and medical devices such as ventilators or personal protective equipment (PPE), would almost certainly offer public health, economic, and national security benefits. For example, stolen intellectual property could give countries a faster path to large-scale inoculation and economic growth, and thereby usher in domestic stability and garner international praise.
The Cyber Centre is aware of cyber threat activity directed against Canada that we assess is almost certainly tied to Canada’s status as a world leader in health and biotechnology. Many of Canada’s companies and research universities are leading global efforts to develop COVID-19 tests, treatments, and vaccines, making them attractive targets.
In mid-April 2020, a Canadian biopharmaceutical company was compromised by a foreign cyber threat actor almost certainly attempting to steal its intellectual property. State-sponsored actors have targeted medical companies and research universities in South Korea,Footnote 19 China,Footnote 20 the US,Footnote 21 and the UK.Footnote 22 as well. On 13 May 2020, the Federal Bureau of Investigation (FBI) and the Cybersecurity and Infrastructure Security Agency (CISA) in the US issued an announcement warning healthcare, pharmaceutical, and research organizations working on the COVID-19 response that they are prime targets for state-sponsored cyber threat actors.Footnote 23
Pharmaceutical and medical equipment companies, as well as medical research organizations, have also been targeted in ransomware attacks. As with front-line medical providers, these organizations are attractive targets for cyber criminals due to the time-sensitivity of their work and their ability to pay the ransom. Between March and April 2020, ransomware attacks were directed at organizations such as these in Canada,Footnote 24 the US,Footnote 25 the UK, Footnote 26 Belgium,Footnote 27 and GermanyFootnote 28.
Supercomputers compromised
Cyber criminals have hijacked supercomputers throughout Europe to mine cryptocurrency. Some of these supercomputers were involved in COVID-19 research efforts, such as modelling the spread of the virus and assisting with the development of treatments and vaccines. As a result, the systems had to be taken offline to be repaired, interrupting the research efforts.Footnote 18
Online influence and fraud
We judge that online influence campaigns will almost certainly continue to spread falsehoods and foment greater skepticism of official statistics and statements regarding the COVID-19 pandemic. Although we do not assess that Canada is a high priority target for online influence activities, that could change quickly, especially in response to increased political tensions with some states. In addition, the US,Footnote 29 UK,Footnote 30 and other countries are a target for online influence campaigns and their information ecosystems are closely intertwined with that of Canada. Canadian law enforcement officials are currently investigating possible links between attacks on cell phone towers in Canada and a COVID-19-related conspiracy theory that ties the disease to 5G technology, which has resulted in attacks on cell phone towers globally.Footnote 31 In April 2020, a disinformation campaign targeted a Canadian-led NATO battle group in Latvia, falsely claiming that one of their contingents had “a high number” of cases of COVID-19.Footnote 32 This activity was almost certainly intended to increase hostility between the Latvian public and the Canadian-led forces stationed there.
Typically, online influence campaigns are aimed at domestic audiences to diffuse dissatisfaction with national pandemic responses or at international audiences in order to blunt and counter international criticism. This can be achieved by spreading false and distorted information, or otherwise shaping narratives on social media that portray rival governments as untrustworthy or inept in their handling of the COVID-19 pandemic. According to an April 2020 report by EUvsDisinfo, a European Union project analyzing disinformation, online influence activity includes the spread of theories that COVID-19 is a hoax, contradictions of official WHO guidance, and incorrect information about potential treatments.Footnote 33 The immediate goal of this type of online influence is to sow confusion and anger, induce mistrust and doubt, and weaken the ability of targeted nations to manage the pandemic. Beyond that, individuals believing these malicious messages may end up putting themselves and others at risk.
The COVID-19 pandemic has also been harnessed by cyber criminals to advertise counterfeit medical suppliesFootnote 34 and elicit fraudulent donations.Footnote 35 The Canadian Anti-Fraud Centre has issued a warning listing many scams related to COVID-19, including fraudulent offers of fast COVID-19 tests for sale, counterfeit products that claim to treat or prevent the disease, and fake online advertisements offering high demand cleaning products.Footnote 36 The FBI has noted multiple cases of government agencies transferring funds to fraudulent sellers in attempts to purchase PPE and other medical equipment and supplies.Footnote 37 In one week, INTERPOL seized more than 34,000 counterfeit and substandard masks alongside other fake products like “corona spray” and “coronavirus medicine”, many of which were being sold online.Footnote 38
Fraud has immediate costs for the victims of these schemes and causes additional losses due to the diversion of resources from legitimate COVID-19 efforts. In many cases, victims never receive any goods, but in others, the distribution of counterfeit and substandard products dangerously diminishes the health sector’s efforts to protect its staff and the public from COVID-19.Footnote 39 We assess that pandemic response efforts will almost certainly continue to be negatively impacted by online fraud activity related to COVID-19, which diverts resources and distributes counterfeit and substandard goods.
Useful resources
For more information on how to mitigate cyber threats, including those related to COVID-19 lures or remote workforce deployments, we recommend visiting the following websites:
- Cyber threats to Canadian health organizations
- Cyber security advice and guidance for research and development organizations during COVID-19
- Canadian Shield – Sharing the Cyber Centre’s threat intelligence to protect Canadians during the COVID-19 pandemic
- COVID-19 Malicious Websites
- Cyber Centre’s advice on cyber hygiene
- Spotting malicious e-mails
- Staying cyber safe while teleworking
- Considerations when using video-teleconference products and services
- Video-teleconferencing
- Cyber security tips for remote work
- Security tips for organizations with remote workers
- Virtual private networks
- Active exploitation of VPN vulnerabilities
- Active exploitation of Citrix vulnerabilities
- Continued threat actor exploitation post pulse secure VPN patching (CISA)
- How to spot misleading information online and what to do about it
- Ransomware: How to prevent and recover
- Protect your organization from malware
- IoT security for small and medium organizations