About this document
Audience
This Cyber Threat Bulletin is intended for the cybersecurity community. Subject to standard copyright rules, TLP:WHITE information may be distributed without restriction. More information on the Traffic Light Protocol.
Contact
For follow up questions or issues please contact CCCS at contact@cyber.gc.ca.
Assessment base and methodology
The key judgements in this assessment rely on reporting from multiples sources, both classified and unclassified. The judgements are based on the Canadian Centre for Cyber Security (CCCS)’s knowledge and expertise in cyber security. Defending the Government of Canada’s information systems provides the Cyber Centre with a unique perspective to observe trends in the cyber threat environment, which also informs our assessments. CSE’s foreign intelligence mandate provides us with valuable insight into adversary behavior in cyberspace. While we must always protect classified sources and methods, we provide the reader with as much justification as possible for our judgements.
Our key judgements are based on an analytical process that includes evaluating the quality of available information, exploring alternative explanations, mitigating biases and using probabilistic language. We use terms such as “we assess” or “we judge” to convey an analytic assessment. We use qualifiers such as “possibly”, “likely”, and “very likely” to convey probability.
The contents of this document are based on information available as of 27 April 2020.
Estimative language
The chart below matches estimative language with approximate percentages. These percentages are not derived via statistical analysis, but are based on logic, available information, prior judgements, and methods that increase the accuracy of estimates.
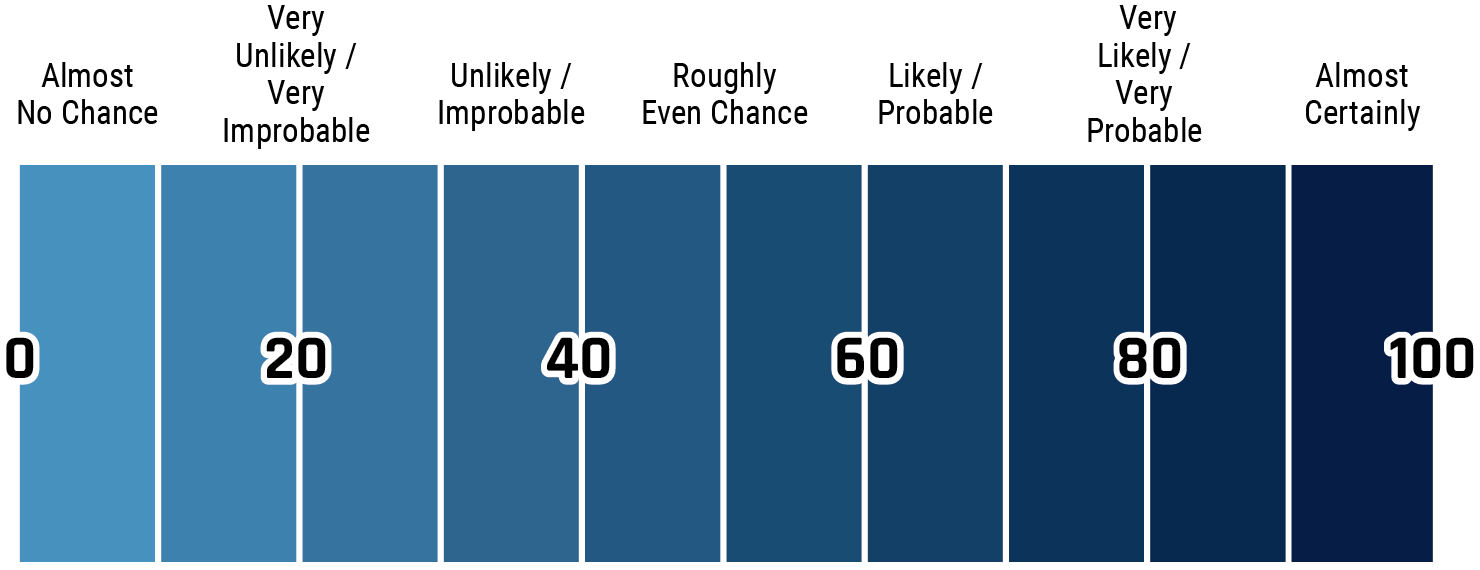
Long description - Estimative language
- Almost no change – 0%
- Very unlikely/very improbable – 20%
- Unlikely/improbable – 40%
- Roughly even chance – 50%
- Likely/probably – 60%
- Very likely/very probable – 80%
- Almost certainly – 100%
Key judgements
- Cyber threat actors of varying motivations and sophistication are taking advantage of the COVID-19 pandemic as a thematic lure or subterfuge for their malicious activities, such as cyberespionage and cybercrime.
- The global health sector is under extreme pressure to mitigate the COVID-19 pandemic. We assess that, almost certainly, ransomware will continue to target healthcare and medical research facilities, jeopardizing patient outcomes and wider public health efforts.
- State intelligence collection requirements have shifted in response to COVID-19. We judge it is almost certain that cyber espionage directed at Canada will continue to attempt to steal Canadian intellectual property relating to COVID-19 medical research, as well as classified information regarding Government of Canada responses.
- We assess that multiple state-sponsored cyber threat actors have very likely reduced staff and temporarily slowed their operational tempo, but that their online operations will increase over the coming year as more traditional espionage activities remain hampered by travel restrictions and social distancing.
- Online influence campaigns continue to erode trust in official statements and figures, weakening public health responses and exacerbating the public anxiety and uncertainty that make COVID-19-themed cyber threats so effective.
- We expect the remote workforce almost certainly to be increasingly targeted by foreign intelligence services and cybercriminals. Cyber threat actors are already attempting to identify individuals working at home employed in areas of strategic interest and exploiting technologies deployed in support of a remote workforce, such as virtual private networks (VPNs) or video-conferencing platforms.
- We assess that it is very likely that authoritarian governments will use COVID-19 as a justification to procure and deploy surveillance technologies against their own citizens and expatriates residing in Canada or Canadians living abroad.
Impact on cyber threat activity
The World Health Organization (WHO) officially declared the novel coronavirus disease 2019 (COVID-19) a global pandemic on 11 March 2020, and cyber threat actors of varying motivations and sophistication have taken advantage of the COVID-19 pandemic in recent months as a thematic lure or subterfuge for their malicious activities, such as cyberespionage and cybercrime.
COVID-19-themed lures
Since at least January 2020, cyber threat actors have developed enticing COVID-19-related content (e.g., epidemiological statistics on infection rates and geographic spread, local and regional public health updates, knowledge of cures or treatments, access to sought-after medical supplies, etc.) to trick victims into clicking on malicious links and attachments. COVID-19 lures are commonly found in phishing email campaigns attempting to distribute information-stealing malware, and to a lesser extent, ransomware, on personal computers and mobile devices.
Most observed COVID-19 lures deliver malware associated with either state-sponsored groups or well-known cybercriminals. COVID-19 lures are increasingly used by fraudsters to advertise counterfeit medical supplies, elicit fraudulent donations, and support other fraudulent schemes. Cyber threat actors know that affected populations are anxious about the future and less likely to act prudently when presented with emails, SMS messages, or advertisements involving COVID-19 that would otherwise seem suspicious.
COVID-19 lures often attempt to replicate or imitate the branding and style of legitimate organizations in order to elicit trust. Cyber threat actors are aware that the names and logos of international organizations or national health agencies are appearing more frequently in the news and on social media, but that most individuals are unfamiliar with their websites and communications. Cyber threat actors are capable of crafting convincing copies of government websites and official correspondence.
Canadian public health responses and initiatives are being repurposed by state-sponsored cyber threat actors and cybercriminals as COVID-19 lures for the purpose of targeting Canadians and Canadian organizations. Recent COVID-19 lures have pivoted to take advantage of the emergency benefits and economic stimulus packages being stood up by governments across North America and Europe.
Notable examples of COVID-19 lures:
- As of 27 April 2020, CCCS was aware of over 120,000 newly registered COVID-19 themed domains, a large proportion of which was considered malicious or related to fraudulent activity. One notable SMS phishing campaign claimed to notify the victims of awaiting a Canadian Emergency Response Benefit (CERB) deposit with a link where they could access their benefits, but only once they divulged personal financial details.
- On 10 March 2020, phishing emails impersonating the Public Health Agency of Canada’s (PHAC) Medical Officer of Health were used to deliver malware embedded in an attachment claiming to be an important COVID-19 update.
- On 23 March 2020, a technical flaw on the US Department of Health and Human Services (HHS) website was used to hide a malicious link, which had been advertised as a COVID-19 self-assessment resource. Users who clicked on the link were redirected to a malicious website hosting malware.
- On 25 March 2020, cybercriminals sent SMS messages pretending to be the Government of Canada, directing individuals to go to the “Canada-alert-covid19[dot]com” website. The malicious website prompted victims to download a malicious application.
As of 27 April 2020, CCCS was aware of over a thousand malicious imitations of Government of Canada (GC) websites using COVID-19-themed lures and provided information to initiate their take down. Most of these malicious impersonations were related to the Canada Revenue Agency (CRA) and the Canadian Emergency Response Benefit (CERB).
Ransomware Targeting of Healthcare and Medical Research Facilities
Cyber threat actors know that the health sector is under intense pressure to slow the spread of COVID-19 by treating existing cases and producing the medical treatments to prevent new ones. Hospitals and other front-line medical services are often vulnerable to malicious cyber threat activity due to limited cybersecurity capacity. Despite recent widely reported promises by leading cybercriminal groups to refrain from targeting health-related organizations, ransomware operators continue to compromise healthcare and medical research facilities in some of the most severely affected countries.
Since 11 March 2020, healthcare and medical research facilities in the UK, US, France, Czech Republic, Spain, and Portugal have been impacted by ransomware. More than ten of these were US hospitals compromised by the Ryuk ransomware, whose operators have targeted Canadian healthcare providers multiple times since October 2019. On 13 March 2020, Brno University Hospital in the Czech Republic, a COVID-19 testing facility, had its operations, including surgeries, disrupted by ransomware.
Ransomware operators often leak documents to retaliate against victims who refuse to pay their ransom demands. On 13 March 2020, REvil ransomware operators leaked internal documents belong to US biotech firm, 10xGenomics, which is currently supplying medical research equipment to laboratories working on COVID-19 treatments.
In early-April 2020, individuals associated with a Canadian university engaged in COVID-19 research and a Canadian provincial government health agency were targeted by COVID-19-themed phishing attacks attempting to deliver ransomware.
COVID-19 and Foreign Intelligence Collection
Given the unexpected spread and severity of the disease, governments almost certainly feel they are operating with inadequate information to craft effective public health and economic responses to the COVID-19 pandemic. As such, foreign intelligence agencies are almost certainly being tasked with new intelligence collection requirements related to the COVID-19 pandemic. State-sponsored cyber threat actors are increasingly targeting the health sector, including government health agencies, almost certainly to obtain intellectual property and other sensitive data pertaining to COVID-19 medical research, but also to attain advanced warning of public health responses (e.g., travel restrictions) under consideration by foreign states. It is also likely that cybercriminals affiliated with affected governments are targeting the health sector to supplement official intelligence collection efforts.
We judge that states are very likely seeking information regarding the COVID-19 pandemic’s effect on military preparedness, particularly in areas with ongoing territorial disputes or geopolitical friction.
CCCS is aware of cyber threat activity directed against Canada that we assess is almost certainly tied to Canada’s reputation as a world leader in health and biotechnology. Many of Canada’s companies and research universities are leading the world’s efforts to rapidly manufacture highly efficient COVID-19 testing kits and develop a COVID-19 vaccine.
Notable examples:
- In mid-April 2020, a Canadian biopharmaceutical company was compromised by a foreign cyber threat actor, almost certainly attempting to steal its intellectual property.
- In March 2020, WHO attributed two phishing campaigns targeting its staff to two separate state-sponsored cyber threat actors.
- On 31 March 2020, a South Korean manufacturer of COVID-19 testing kits prevented a targeted intrusion attributed to a foreign cyber threat actor, very likely attempting to steal its intellectual property.
Cyber Threat Activity against Canadians Working from Home
The COVID-19 pandemic has caused huge swathes of the global workforce to immediately vacate the office and set-up remote workstations from home. Many Canadians, including federal and provincial government employees across the country, are accessing sensitive data through virtual private networks (VPNs) and cloud computing solutions for the first time, and many are using their personal devices and home Wi-Fi networks that are poorly secured in comparison to corporate IT infrastructure.
Cyber threat actors are increasingly attempting to identify and exploit the devices of individuals working at home, particularly targeting those who are employed in areas of strategic interest. Since January 2020, CCCS and its foreign counterparts have observed multiple cyber threat actors leveraging known vulnerabilities in popular VPNs (e.g., Pulse Secure, Fortinet, and Palo Alto) and cloud-hosted applications (e.g., Citrix) to establish persistent access to networks in Canada and other countries.
Since mid-March 2020, CCCS has observed an increase in the use of Microsoft Remote Desktop Protocol (RDP) to support remote work options. Poorly secured RDP servers are among the top initial infection vectors for cyber threat actors, accounting for a substantial number of observed ransomware attacks.
Similarly, the recent surge in downloads of chat and video-conferencing platforms such as Microsoft Teams, Google Hangouts, and Zoom has prompted cyber threat actors and security researchers alike to channel their energies into identifying vulnerabilities that would enable cyber espionage. Zoom faced challenges to their reputation after security researchers scrutinized the platform. For example, the University of Toronto’s Citizen Lab reported that user communications, including encryption keys, may be routed through Zoom’s servers in China even when all participants are located outside of China. Beyond that, cyber threat actors are also trying to victimize targets by luring them with fake chat and video-conferencing platforms.
COVID-19 Online Influence Campaigns
State censorship and influence campaigns continue to spread falsehoods and foment greater skepticism of official figures and statements regarding the COVID-19 pandemic. While many online influence campaigns are aimed at mollifying domestic audiences or reputation management, others serve to portray rival governments as untrustworthy or too inept to handle the COVID-19 pandemic in order to stoke public unrest or weaken public health responses.
We do not assess Canada or Canadians to be a high-priority target of COVID-19-related influence campaigns. Nevertheless, the purposeful dissemination of inaccuracies regarding the origins, spread, or mitigation of COVID-19 can only work to undermine the efforts of Canadian and global public health responses. Many influence campaigns are aimed at Canadian allies, including those hosting significant contingents of Canadian diplomatic and military personnel who will very likely be affected by outbreaks of public unrest or disrupted public health responses in those countries.
Notable examples:
- On 20 February 2020, a forged document purportedly drafted by the Ukraine’s Ministry of Health was emailed across Ukraine, claiming that five Ukrainians had been diagnosed with COVID-19. Simultaneously, social media circulated rumours that Ukrainian evacuees returning from China were also infected with COVID-19. Despite multiple official statements stating that no cases of COVID-19 had occurred in Ukraine and that all evacuees were confirmed healthy, panic spread across the country, resulting in multiple protests, clashes with police, and blockades of hospitals imagined to be quarantine facilities for infected Ukrainians.
- On 16 March 2020, the US HHS website was slowed by a DDoS attack. US officials stated that a “foreign actor” conducted the DDoS, which coincided with a large-scale influence campaign that flooded US SMS, email, and social media services with claims of an impending US national quarantine.
- On 22 April 2020, a publicly available European External Action Service report stated that they continued to observe “a convergence of disinformation narratives” among several states. One of these disinformation narratives portrays the origins of the virus as a US biological weapon.
What to expect moving forward
Continued Rise in COVID-19 Lures
We assess that the use of COVID-19 lures will very likely rise as the pandemic unfolds and captures the public interest. In the immediate future, it is almost certain that cybercrime actors will continue to imitate COVID-19 economic stimulus and benefit programs, such as CERB, to target individuals and businesses into divulging financial data or downloading malicious software. This will very likely be done by impersonating government correspondence or websites, reminiscent of CRA-themed lures commonly observed during tax season. Cybercriminals appear to be becoming more adept at targeting severely affected regions and municipalities with COVID-19 lures as well. As social distancing efforts begin to “plank the curve” and the wider public grows increasingly anxious for a return to normalcy, we expect that cybercriminals will likely begin crafting phishing lures which play on an increased appetite for information around COVID-19 vaccine development and production.
Ongoing Ransomware Operations against Canada and Our Health Sector
We assess that the Canadian health sector will almost certainly continue to be targeted by ransomware campaigns of varying sophistication in the immediate future. Ransomware attacks against healthcare providers, research facilities, and medical manufacturers will have negative consequences on patient care and hinder the development and production of Canadian medical research and domestic supply chains.
Shifting Foreign Intelligence Collection Efforts and Priorities
We judge that most states, especially those will high rates of infection or ambitions to improve their international standing, will almost certainly prioritize COVID-19-related intelligence collection for the foreseeable future. It is almost certain that cyber threat actors will continue in their attempts to steal Canadian intellectual property under development to combat COVID-19 in order to support their own domestic public health response or profit from its illegal reproduction by their own firms.
We asses that state-sponsored cyber programs that were under significant economic pressure prior to the pandemic due to international sanctions will likely attempt to supplement dwindling state revenues through cybercrime. Many authoritarian governments, some poorly prepared to weather even a short-lived recession, will very likely shelter their security and intelligence services’ budgets as they rely on these organizations to ensure regime stability. We judge that increased state-sponsored or state-tolerated cybercrime will very likely continue to pose a significant risk to Canadian financial institutions.
We judge that it is likely that multiple state-sponsored cyber threat actors have temporarily slowed their operational tempo as a result of COVID-19 shutdowns. However, we expect that most states will almost certainly be increasingly reliant on online operations to gather foreign intelligence over the coming year, particularly if more traditional avenues of intelligence collection continue to be significantly hampered by global travel restrictions and the sustained disruption of global commerce, international agencies, and academic institutions.
Expanding Foreign State Use of Surveillance Technologies
It is very likely that authoritarian governments will attempt to procure and deploy foreign surveillance technologies under the guise of combating the COVID-19 pandemic. In the past, telecommunications surveillance products—such as those of surveillance technology company NSO Group—have been marketed to authoritarian governments, who have used them to covertly target Canadians in Canada. NSO Group claims that at least a dozen countries are currently testing their mobile application, which aggregates device data to map and analyze the spread of COVID-19.
Many national public health efforts to “plank the curve” of COVID-19 continue to rely on bulk geolocation data derived from telecommunications providers and third-party companies. South Korea, which has been praised for its COVID-19 response, aggregated smartphone geolocation data with CCTV video and credit card transactions to track confirmed cases and map out areas where others could have encountered infected individuals.
Technology firms such as Google (Figure 1) and Facebook are making anonymized, aggregated location data freely available to monitor social distancing efforts. On 10 April 2020, Apple and Google announced a partnership to develop and deploy COVID-19 “contact tracing” technology across their platforms, which uses Bluetooth to share and track anonymized records of individuals that one has been in contact with as substitute for aggregating and correlating personal location data.
We expect that privacy concerns will likely initiate passionate public debates, including in Canada, on the expanding use and effectiveness of surveillance technologies to combat the ongoing COVID-19 pandemic. It is very likely that influence campaigns will manipulate privacy concerns in order to sow discord and erode trust in public institutions.
Figure 1 – Publicly available mobility trends of Canadians
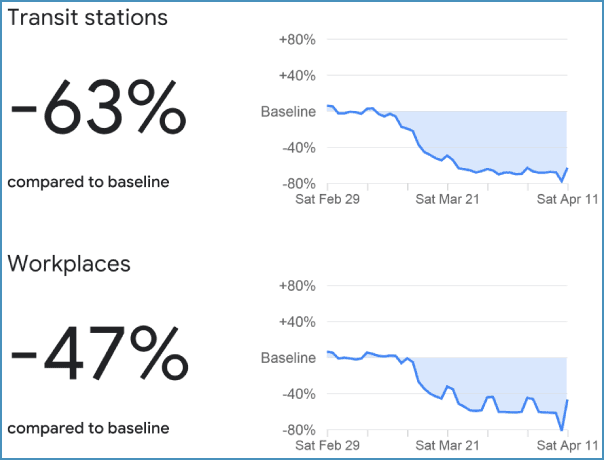
Long description - Publicly available mobility trends of Canadians
Figure 1 illustrates publicly available mobility trends of Canadians derived from Google location data (google.com/covid19/mobility). The data shows a decrease of 63 per cent of Canadians using public transport and a decrease of 47 per cent of Canada going to workplaces since mid-March 2020.
Useful resources
For more information on how to mitigate cyber threats, including those related to COVID-19 lures or remote workforce deployments, we recommend visiting the following websites:
- Cyber threats to Canadian health organizations
- Canadian Shield – Sharing the Cyber Centre’s Threat Intelligence to Protect Canadians During the COVID-19 Pandemic
- Cyber Centre’s advice on Cyber Hygiene
- Spotting malicious e-mails
- Staying cyber safe while teleworking
- Cyber Security Tips for Remote Work
- Considerations when using video-teleconference products and services
- Active exploitation of VPN vulnerabilities
- Active Exploitation of Citrix Vulnerabilities
- Vulnerabilities exploited in VPN products used worldwide (NCSC Alert)
- Continued threat actor exploitation post Pulse Secure VPN patching (CISA)
- How to spot misleading information online and what to do about it