Alternate format: Targeted manipulation: Iran's social engineering and spear phishing campaigns (PDF, 545 KB)
About this report
This report advises on the threat from social engineered spear phishing campaigns by Iranian state-sponsored actors. It is intended for experts and professionals that work in fields that may be of strategic interest for Iran, cyber security professionals, and the general reader with an interest in cyber security. For guidance on technical mitigation of these threats, consult the Canadian Centre for Cyber Security’s (Cyber Centre) guidance or contact the Cyber Centre.
Sources may use TLP:CLEAR when information carries minimal or no foreseeable risk of misuse, in accordance with applicable rules and procedures for public release. Subject to standard copyright rules, TLP:CLEAR information may be distributed without restriction. You can find more information on the Traffic Light Protocol at the Forum of incident response and security teams website.
Contact
For follow-up questions or issues please contact the Cyber Centre at contact@cyber.gc.ca.
Assessment base and methodology
The key judgements in this assessment rely on reporting from multiple sources, both classified and unclassified. The judgements are based on the knowledge and expertise in cyber security of the Cyber Centre. Defending the Government of Canada’s information systems provides the Cyber Centre with a unique perspective to observe trends in the cyber threat environment, which also informs our assessments. The Communications Security Establishment’s foreign intelligence mandate provides us with valuable insight into adversary behaviour in cyberspace. While we must always protect classified sources and methods, we provide the reader with as much justification as possible for our judgements.
Our judgements are based on an analytical process that includes evaluating the quality of available information, exploring alternative explanations, mitigating biases and using probabilistic language. We use terms such as “we assess” or “we judge” to convey an analytic assessment. We use qualifiers such as “possibly”, “likely”, and “very likely” to convey probability.
The assessments and analysis are based on information available as of February 2, 2024.
Estimative language chart
The chart below matches estimative language with approximate percentages. These percentages are not derived via statistical analysis, but are based on logic, available information, prior judgements, and methods that increase the accuracy of estimates.
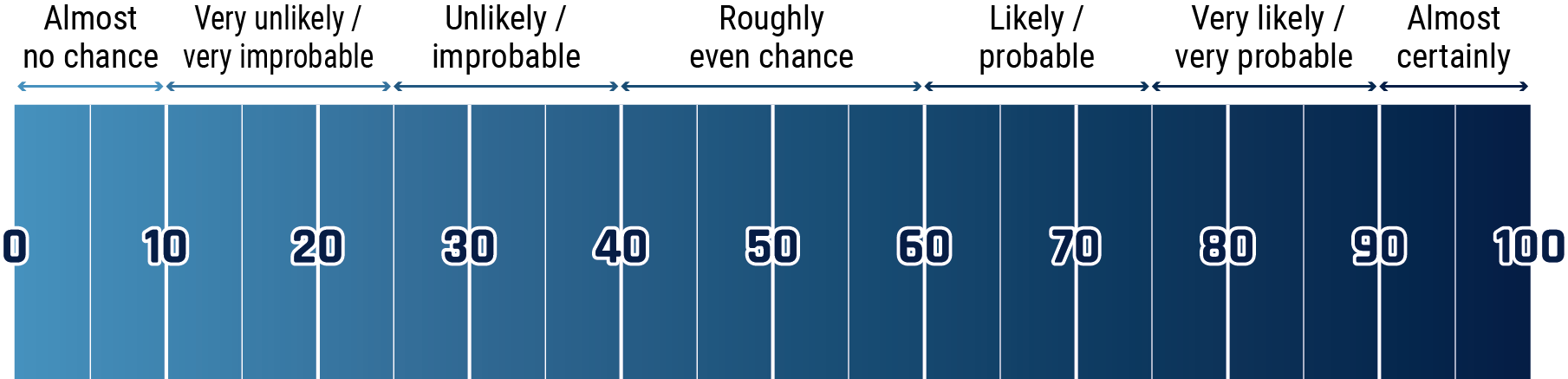
Long description - Estimative language chart
- 1 to 9% Almost no chance
- 10 to 24% Very unlikely/very improbable
- 25 to 39% Unlikely/improbable
- 40 to 59% Roughly even chance
- 60 to 74% Likely/probably
- 75 to 89% Very likely/very probable
- 90 to 99% Almost certainly
Key judgements
- We assess that Iranian cyber threat actors continue to be particularly sophisticated in social engineering and in using it to enhance their spear phishing capabilities.
- We assess that Iranian cyber threat actors customize and enhance the effectiveness of their social engineering campaigns by developing compelling personas, building rapport with targets over longer periods of time and using enticing, highly emotive content related to timely geopolitical issues or traumatic events.
- We assess that Iranian cyber threat actors prioritize their social engineering and spear phishing efforts against experts that have information considered to be of political, economic or military intelligence value to Iran.
Introduction
We assess that Iranian cyber threat actors are particularly sophisticated in social engineering and in using it to enhance their spear phishing capabilities. Iranian actors support their spear phishing operations through techniques such as creating compelling personas, using enticing or emotive lures, and building rapport with their targets over long periods of time. Iranian social engineering efforts focus on using professional interactions on social media platforms to gain information about organizations related to Iran’s political, economic and military interests, particularly in the aerospace, energy, defence, security and telecommunications sectors.Footnote 1 Iranian actors use social engineering and spear phishing operations against softer targets like personal email and social media accounts as a method of collecting information from, or gaining access to, even hardened government and organizational networks.
What is social engineering?
Social engineering is the attempt to manipulate a person into doing something that is not in their best interests like divulging information (e.g. login credentials, sensitive information, etc.).
There are 5 features that make social engineering successful:
- Reciprocity: People feel obligated to discharge previous perceived debts
- Authority: People respond to authority figures
- Scarcity: People value things they perceive as scarce
- Consistency: People act to maintain their social image
- Social proof: People tend to trust people they perceive as similar to themselves
Cyber threat actors leverage social media sites to feign legitimacy and deceive victims to enable spear phishing operations.
Iran’s approach to sophisticated social engineering campaigns
We assess that Iranian cyber threat actors customize and enhance the effectiveness of their social engineering campaigns by developing compelling personas, building rapport with targets over longer periods of time and using enticing, highly emotive content related to timely geopolitical issues or traumatic events.
Figure 1: The social engineered spear phishing process
Actors construct false persona on multiple social media sites
Persona interacts with the target, often building trust and relating on shared interests
Actors send malicious link or file and/or attempt to compromise device
Creating compelling personas
Iranian cyber threat actors create and employ fake personas to build relationships with their targets and establish trust. They typically develop professional relationships or relationships around the targets’ interests. Personas allow for a curated and interactive approach to establishing trust and legitimacy with targets, especially when more individuals’ “professional and social selves” are now online and not as distinguishable from their “offline selves”. We assess that Iranian cyber threat actors very likely use attractive female personas to manipulate their targets.Footnote 2 Further, we assess that Iranian cyber threat actors likely leverage previously compromised and spoofed email accounts to add a perceived legitimacy to their personas and for subsequent lures.
Iranian cyber threat actors have used fake personas to target individuals from a wide variety of professional fields including:
- defence contractors
- aerospace employees
- energy sector employees
- journalists
- academics
- researchers
- activists
- politicians
- diplomats
- civil society groupsFootnote 1Footnote 2Footnote 3
Case study 1: Aerobics instructor from Liverpool or Iranian social engineer?
An Iranian cyber threat actor used a false persona to pose as an aerobics instructor and personal trainer named Marcella Flores. The false persona established a months-long relationship with the employee of an aerospace defence contractor.
The false persona nursed the digital relationship over multiple corporate and personal communication platforms. The persona then delivered malware to the target’s machine through a malicious Excel spreadsheet that appeared to be a benign “Diet Survey” document.Footnote 4
Case study 2: Mia Ash
Mia Ash was a fake persona used by Iranian cyber threat actors to target organizations in the Middle East from 2016 to 2017. Ash claimed to be a 30-year-old British professional photographer. Her profile was built using stolen pictures, likely from an Instagram account of a legitimate photographer. She had a presence on Facebook, Blogger and LinkedIn.
The persona used LinkedIn to contact an employee at a targeted organization and exchanged messages with the target about their professions, photography and travels, after which she encouraged the target to add her on Facebook. Correspondence continued via WhatsApp, email and Facebook. After a few weeks, she sent a malicious Excel document for a photography survey, encouraging the target to open it at work using their corporate email. Threat actors likely leveraged the persona to gain access to a targeted organization because the initial phishing campaign was unsuccessful.
Repeat use of personas
Iranian actors will often use personas multiple times which likely demonstrates a sustained effort in the development of these personas and their networks.Footnote 2 The following examples demonstrate how Iranian actors reuse personas to achieve their objectives.
- Female Persona A
- Winter 2020: Iranian actors used Persona A to conduct a social engineering operation against a U.S. person.
- Summer 2020: Actors used Persona A again to conduct spear phishing and social engineering operations against multiple individuals, using scholarly and news-themed emails where the targets were directed toward malicious documents via links or attachments.
- Female Persona B
- Spring 2020: Iranian cyber threat actors used Persona B to befriend a foreign national on LinkedIn. The cyber threat actors later compromised the target’s device and exfiltrated sensitive personal information and content from the device.
- Summer 2020: Iranian cyber threat actors used Persona B to impersonate a recruiter to target an employee of a U.S. cleared defence contractor and obtained target’s resume. The persona was also active on LinkedIn, making several connections to personnel of various companies.
- Female Persona C
- Summer 2022 to summer 2023: Iranian actors used the Persona C on Facebook to conduct a social engineering campaign against a Defense Industrial Base employee. Persona C shared a website with the employee based around a shared hobby.
- Spring 2023: Iranian actors used Persona C to target several employees of Defense Industrial Base Companies, based on their company affiliation on Facebook. Persona C claimed to be conducting research and sent targets a questionnaire.
- Female Persona D
- Winter 2021 to fall 2022: Iranian actors targeted a Europe-based defence sector employee using Persona D on a career-oriented social networking site. After establishing trust, communications moved to email, where the persona sent a malicious document and encouraged the target to add information.
- Spring 2023: Iranian actors almost certainly used Persona D to target a specific personal email account with a spear phishing email encouraging the victim to open the malicious link and then enter a provided password.
- Female Persona E
- Fall 2022 to fall 2023: Iranian actors used Persona E across multiple social media platforms posing as a journalist questioning targets on human rights issues in Iran. The persona’s likely intention was to send malicious files to the target.
- Summer to fall 2023: Iranian actors used multiple personas (including Persona E) in a combined spear phishing and social engineering operation targeting employees in the nuclear sector.
Targeting emotional vulnerabilities and building trust: Operations around traumatic events
Targeting veterans with post-traumatic stress disorder (PTSD)
In 2020, Iranian cyber threat actors conducted a PTSD-themed social engineering campaign against defence contractors and government officials using a fictitious psychologist LinkedIn persona. The persona was seeking inquiries from military service members suffering from PTSD as a result of combat experience. The actor solicited targets into visiting probable malicious links and into providing work-related contact information.
Iranian cyber threat actors use personas to develop trust with a target by sharing their concerns around major traumatic events and tragedies. For example, Iranian cyber threat actors had reportedly run an Israel-Hamas war-themed campaign creating a fake website for the “Bring Them Home Now” movement, which calls for the return of Israeli hostages held by Hamas, where the website would eventually lead to downloading a malicious payload.
In October 2022, after the death of Mahsa Amini and ensuing protests in Iran, Iranian cyber threat actors used a false Twitter (now X) persona, Sara Shokouhi, to conduct a spear phishing campaign targeting female protestors, political activists and human rights researchers inside and outside of Iran. The persona reached out to victims, purportedly on behalf of the U.S. Atlantic Council think tank, to gain trust and build rapport with victims over several weeks after which it attempted to either steal credentials or deploy malware on their computer or mobile device.Footnote 5
Offering false professional opportunities and collaboration
Iranian cyber threat actors appeal to shared professional interests, offering to collaborate with the target, gaining more trust and access to information throughout the process. For many fields, including academia, journalism, research, activism and NGOs, online collaboration is considered routine. Targets in these professions are valuable not only for their knowledge, but also for their networks of contacts and the places and people that they may have access to.
Job opportunities
Iranian cyber threat actors have run many operations using personas posing as recruiters and employees of companies from the countries in which their targets were located to offer targets prospective job opportunities. These operations typically target U.S. defence contractors in the Middle East and subcontractors associated with larger defence companies.Footnote 2
Think tanks and research institutes
Iranian actors impersonated the president of the U.S.-based Middle East Institute and contacted Iranian and non-Iranian activists asking to establish a partnership with the target and collaborate in the target’s area of expertise. After building trust with the target over correspondence, actors invited them to participate in a virtual meeting, sending a malicious link to steal the target’s credentials.Footnote 6
Conferences
In a 2021 operation to gather strategic insights on relations with Tehran, Iranian cyber threat actors masqueraded as scholars from the University of London’s School of Oriental and African Studies (SOAS) organizing a conference. Personas targeted experts in foreign policy, journalism, and academics specializing in Middle East politics. They established relationships and communicated with targets eventually leading them to a conference registration link hosted on a compromised website.Footnote 2
Iranian cyber threat actors reportedly targeted Human Rights Watch staff members, journalists and human rights activists using WhatsApp, claiming to be from a Lebanon-based think tank, inviting recipients to a conference. The actor impersonated an individual who had previously worked at the think tank and used a similar format to the think tank’s previous invitations.Footnote 2Footnote 3
Media and expertise
Iranian cyber threat actors have used journalistic personas on multiple occasions to conduct intrusion or influence operations against targets. Reporting in 2020 indicates that Iranian actors developed fake personas that spoofed real journalists from major news entities including the New York Times, CNN and The Wall Street Journal. Actors would engage with victims driving them to encrypted chat platforms like WhatsApp, eventually moving to fake video conferences where presumably the victim would continue to be compromised.Footnote 3
Outlook
The post-Covid-19 pandemic tendency for corporations and organizations to move more activities online, such as conferences, recruitment, training and public talks is likely providing, and will continue to provide, Iranian cyber threat actors (and others) more opportunities to conduct social engineering operations.
Advances in AI technology, such as synthetically created images and voice, could enable Iranian cyber threat actors to create more convincing online personas. In early February 2024, Iranian actors interrupted television streaming services in the UAE using a deepfake newsreader delivering a report on the war in Gaza.Footnote 7
Given Iranian cyber threat actors’ tendencies to appeal to those interested or involved in current events, these social engineering techniques could be combined with Iran’s cyber-enabled information operations. Iranian cyber threat actors have employed information operations during the Covid-19 pandemicFootnote 8 and increased such operations since the onset of the Israel-Hamas war in October 2023. Iranian information operations have increasingly targeted international audiences, particularly those in the West.Footnote 9 We assess that Iran could likely combine these information operations with social engineering campaigns to target individuals or organizations concerned about the conflict.
Iran continues to strengthen its operational capacity for social engineering through procuring the infrastructure required to conduct sophisticated social engineering campaigns, establishing new vectors of communication with targets, building networks of personas and training.
Further reading
The Cyber Centre regularly publishes advice and guidance to help Canadians and Canadian organizations protect themselves against common cyber threats. This includes some of the threats outlined in this assessment such as spear phishing and social engineering.
Please refer to the following online resources for more information and for useful advice and guidance:
- Don't take the bait: Recognize and avoid phishing attacks - ITSAP.00.101
- Spotting malicious email messages - ITSAP.00.100
- Social engineering - ITSAP.00.166
- How to identify misinformation, disinformation, and malinformation - ITSAP.00.300
- Artificial Intelligence - ITSAP.00.040
- Preventative security tools - ITSAP.00.058