Cryptographic agility is a concept of best practice that enables cryptographic algorithms used in applications and protocols to be interchanged easily to ensure systems remain secure if new cryptographic vulnerabilities are discovered. This is done primarily through configuration without requiring major software or hardware updates. Agile products must have streamlined software and firmware upgrade capabilities to support cases where all configuration options have been exhausted. To enable a phased transition, agile products should retain interoperability with other systems. Agile products should retain any and all applicable validations and certifications, subject to configuration. Agility relies upon organizational processes and policies that maintain an inventory of locations and uses of cryptographic algorithms and products within an organization to facilitate quick, easy, and complete transitions as needed.
Why is cryptographic agility important?
Over time, breakthroughs in cryptographic research and computing can leave cryptographic algorithms with less strength than their intended design. Legacy applications may employ weak cryptography that can be difficult to upgrade. Vendors with existing support contracts may be unable to react quickly enough to implement and deploy new cryptographic algorithms in response to Common Vulnerability and Exposures (CVE) reports.
A major cryptographic transition is expected in the near future to mitigate against the threat of quantum computers. Much of the public key cryptography in use by products today will be vulnerable to a sufficiently powerful universal quantum computer. Cyber security products that support cryptographic agility can help your organization through this transition.
How does cryptographic agility work?
Cyber security products that are designed with cryptographic agility in mind have access to multiple cryptographic algorithms and allow system owners to configure the product to use or prefer certain algorithms. When configuration options are exhausted, these security products have streamlined software and firmware upgrade processes that provide new configuration options. Cryptographically agile systems also have policies and processes in place to ensure configuration changes, as well as software and firmware updates, are quickly identified.
Network security protocols often negotiate which cryptographic algorithms to use, thus allowing endpoints to be configured differently. The ability to set preferences in product configuration for cryptographic algorithms allows for a phased approach to migrating equipment and applications which maintains interoperability.
For more information on the quantum threat, see Addressing the quantum computing threat to cryptography (ITSE.00.017) and Preparing your organization for the quantum threat to cryptography (ITSAP.00.017).
Cryptographic agility in action
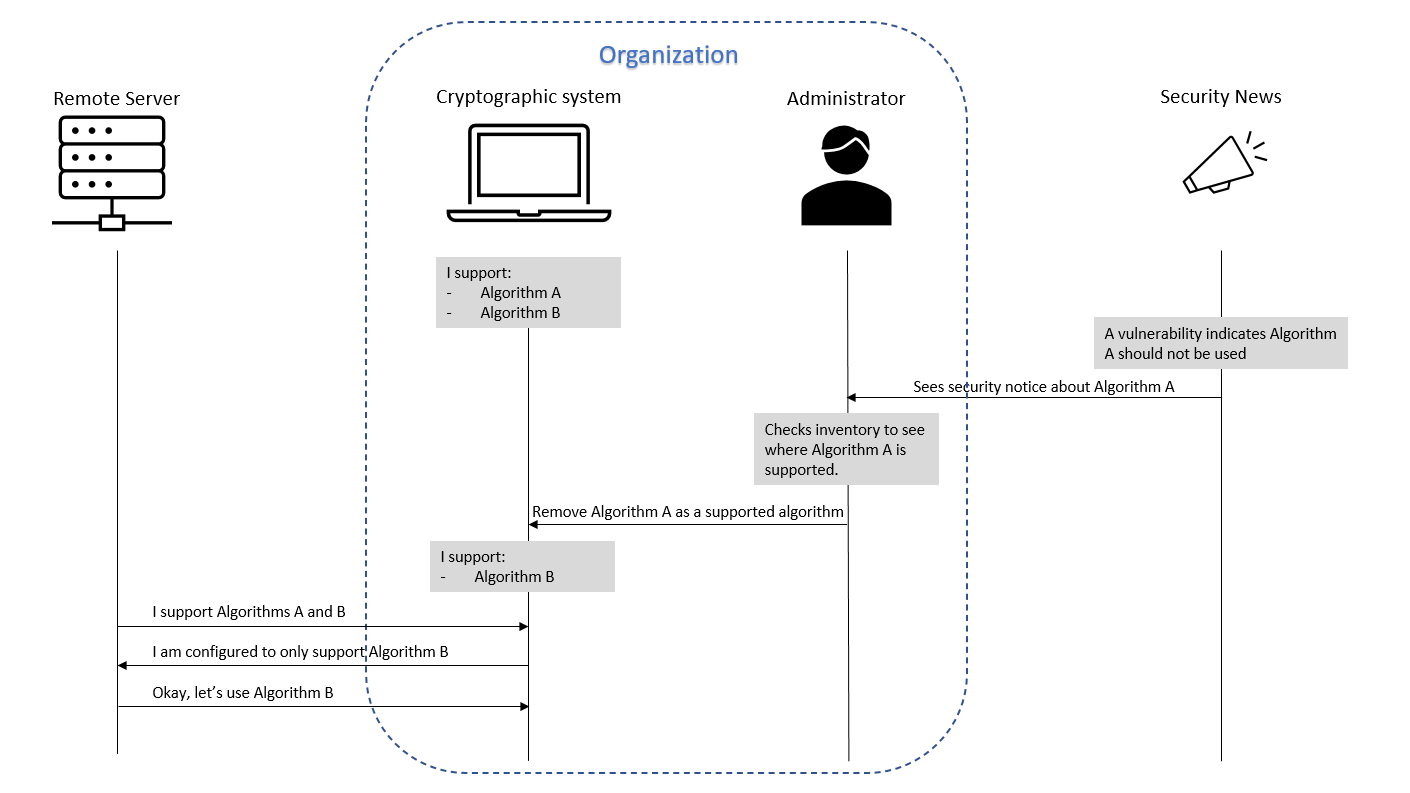
Long description - Figure 1
Figure 1 is a diagram that describes an example of how a cryptographically agile system responds to a new vulnerability found in an algorithm that it currently supports. It shows how the detection of the vulnerability changes the configuration of the cryptographically agile system and changes the interactions with the system moving forward.
There are four icons at the top of the diagram to represent the following items:
- “Remote Server”
- “Cryptographic system”
- “Administrator”
- “Security News”
The administrator and cryptographic system items are grouped together to demonstrate they are within an organization, while the remote server and the security news entities are outside of an organization. The diagram follows the time progression of a cryptographically agile system identifying a vulnerability within a supported algorithm and responding swiftly. The steps are as follows:
- The starting state of the cryptographic system includes a list of the cryptographic algorithms that are currently supported.
- A vulnerability is found in a specific algorithm, call it Algorithm A, by someone outside of the organization and a security notice is posted publicly by the Security News entity.
- This security notice is seen by the administrator of the cryptographic system. The administrator is responsible for maintaining, updating, and properly configuring the cryptographic system.
- The administrator finds that Algorithm A is currently supported by the cryptographic system and subsequently reconfigures the cryptographic system to remove Algorithm A from the supported algorithms.
- An updated set of algorithms that are supported by the cryptographic system moving forward are shown, which indicates the administrator has successfully removed Algorithm A from the supported algorithms. By this step the cryptographic system has successfully responded to the vulnerability with a quick configuration change, a capability possible due to its cryptographic agility. The next steps show how these changes effect future interactions between this cryptographic system and a remote server.
- There is an initial interaction between a remote server and the cryptographic system where the first step is to agree on which cryptographic algorithm to use in their communications. The remote server has sent a list of the algorithms they can support.
- The cryptographic system responds to the remote server with the sub-list containing the algorithms which they also support. That sub-list does not contain Algorithm A as the cryptographic system no longer supports it after the administrator’s change.
- The remote server then selects one of the common algorithms from the sub-list it received from the cryptographic system to use moving forward in their interactions.
What cryptography should I be using now?
When selecting a vendor, ensure they use standardized cryptography with an implementation certified under an independent assurance program (e.g. Cryptographic Module Validation Program [CMVP] and Common Criteria [CC]). Guidance on cryptographic algorithms and protocols can be found in two publications from the Cyber Centre: Cryptographic Algorithms for UNCLASSIFIED, PROTECTED A, and PROTECTED B Information (ITSP.40.111) and Guidance on Securely Configuring Network Protocols (ITSP.40.062). These documents will provide guidance on the transition to quantum-safe cryptography once it is standardized.
Does my organization support cryptographic agility?
To determine whether the products currently deployed in your organization are cryptographically agile, you should complete the following actions:
- Create an inventory of your products that use cryptography.
- Ask your product vendors how they support cryptographic agility. If they do not, request details on their plans to implement agility in future releases.
- Confirm whether your vendors use standardized, validated cryptography (e.g. validated modules under the Cryptographic Module Validation Program) in current and future agile products.
- Determine if your organization has policies and procedures in place in your IT change management activities to support cryptographic agility.
Creating an inventory of all the cryptography used in a large enterprise may be challenging. There is likely cryptography within products that you aren’t aware of.
Some vendors offer products for enterprises that can scan systems or networks and report on cryptography that may need to be replaced. Standard security considerations and practices should be followed when deploying tools that monitor sensitive components like those employing cryptography.
Becoming cryptographically agile
We recommend your organization take the following steps to help become cryptographically agile:
- Inventory your products that use cryptography.
- Implement new policies and procedures in your IT change management activities to maintain this inventory on an on-going basis and manage any configuration changes related to cryptographic agility.
- Ask the vendors of your cryptographic products if they support cryptographic agility. Understand their software and firmware upgrade policies and procedures for any necessary large agility updates.
- Develop a transition plan for any non-agile products, including any legacy cryptography, to upgrade to products that support cryptographic agility.
- Create a procurement policy to ensure cryptographic agility is considered in future purchases.
- Ensure your agility plan uses standardized cryptographic algorithms such as those recommended in ITSP.40.111 and ITSP.40.062 and that the implementations of the cryptographic algorithms have been validated under the Cryptographic Module Validation Program.
Learn more
If you want to learn more about cyber security topics, please check out the following publications on our website.
- Using encryption to keep your sensitive data secure (ITSAP.40.016)
- Preparing your organization for the quantum threat to cryptography (ITSAP.00.017)
- Preventative security tools (ITSAP.00.058)
- Implementation guidance: Email domain protection (ITSP.40.065)
- Cyber security considerations for consumers of managed services (ITSM.50.030)