Alternate format: Cyber threat bulletin: Cyber threat activity related to the Russian invasion of Ukraine (PDF, 863 KB)
About this document
Audience
This Cyber Threat Bulletin is intended for the cyber security community. Subject to standard copyright rules, TLP:WHITE information may be distributed without restriction. You can find more information on the Traffic Light Protocol at the Forum of incident response and security teams website.
Contact
For follow up questions or issues please contact the Canadian Centre for Cyber Security at contact@cyber.gc.ca.
Table of contents
- About this document
- Key judgements
- Russian and Russia-linked cyber activity within Ukraine
- Notable Russian and Russia-linked cyber activity beyond Ukraine
- Non-state actors targeting Russia
- Key players engaged in this cyber activity
- Key indicators associated with cyber scenarios
- Mitigating risk, raising awareness, and increasing cyber security
- Footnotes
Assessment base and methodology
The key judgements in this assessment rely on reporting from multiples sources, both classified and unclassified. The judgements are based on the knowledge and expertise in cyber security of the Canadian Centre for Cyber Security (the Cyber Centre). Defending the Government of Canada’s information systems provides the Cyber Centre with a unique perspective to observe trends in the cyber threat environment, which also informs our assessments. The Communications Security Establishment (CSE)’s foreign intelligence mandate provides us with valuable insight into adversary behavior in cyberspace. While we must always protect classified sources and methods, we provide the reader with as much justification as possible for our judgements.
Our judgements are based on an analytical process that includes evaluating the quality of available information, exploring alternative explanations, mitigating biases and using probabilistic language. We use terms such as “we assess” or “we judge” to convey an analytic assessment. We use qualifiers such as “possibly”, “likely”, and “very likely” to convey probability.
The contents of this document are based on information available as of June 22, 2022.
Note: These percentages are not derived via statistical analysis, but are based on logic, available information, prior judgements and methods that increase the accuracy of estimates.
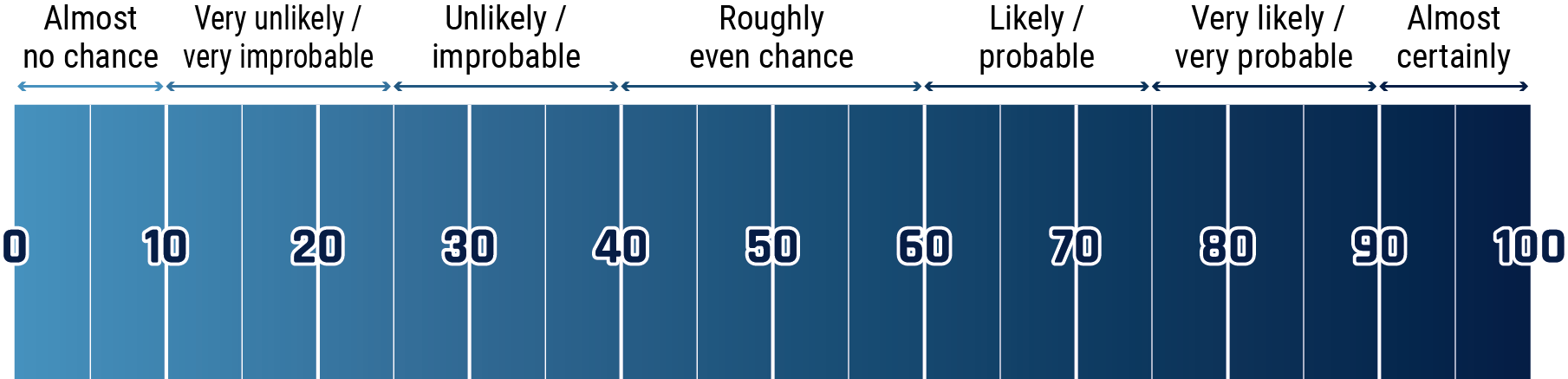
Long description - Estimative language chart
- 1 to 9% Almost no chance
- 10 to 24% Very unlikely/very improbable
- 25 to 39% Unlikely/improbable
- 40 to 59% Roughly even chance
- 60 to 74% Likely/probably
- 75 to 89% Very likely/very probable
- 90 to 99% Almost certainly
Key judgements
- We assess that the scope and severity of cyber operations related to the Russian invasion of Ukraine has almost certainly been more sophisticated and widespread than has been reported in open sources
- We assess that Russian cyber operations have almost certainly sought to degrade, disrupt, destroy, or discredit Ukrainian government, military, and economic functions, secure footholds in critical infrastructure, and to reduce the Ukrainian public’s access to information Footnote 1
- We assess that Russian state-sponsored cyber threat actors will almost certainly continue to perform actions in support of the Russian military’s strategic and tactical objectives in Ukraine
- We assess that Russian state-sponsored cyber threat actors have almost certainly increased cyberespionage targeting of North Atlantic Treaty Organization (NATO) countries in response to NATO’s support for Ukraine
- We assess that Russia is almost certainly in the process of developing cyber capabilities against targets in the European Union (EU) and NATO, including the United States (US) and Canada Footnote 2
Russian and Russia-linked cyber activity within Ukraine
We assess that Russian cyber operations have almost certainly sought to degrade, disrupt, destroy, or discredit Ukrainian government, military, and economic functions, secure footholds in critical infrastructure, and to reduce the Ukrainian public’s access to information.Footnote 3 Russian state-sponsored cyber threat actors will almost certainly continue to perform actions in support of the Russian military’s strategic and tactical objectives in Ukraine.
Since the 2014 Russian annexation of Crimea, Ukraine has significantly improved its cyber security posture, including with recent assistance from European Union (EU) and Five Eyes (Australia, Canada, New Zealand, United Kingdom, and US or FVEY) governments and technology companies.Footnote 4
Following Russia’s invasion of Ukraine on February 24, 2022, likely Russian threat actors conducted several disruptive and destructive computer network attacks against Ukrainian targets, including Distributed Denial of Service (DDoS) attacks and the deployment of wiper malware against various sectors, including government, financial, and energy. Cyber operations have often coincided with conventional military operations.
To date, there are eight tracked malware families that Russia-linked cyber threat actors have used for destructive activity against Ukraine: WhisperGate/Whisperkill, FoxBlade (HermeticWiper), SonicVote (HermeticRansom), CaddyWiper, DesertBlade, Industroyer2, Lasainraw (IsaacWiper) and FiberLake (DoubleZero).Footnote 5
In mid-April, Russian state-sponsored cyber threat actors launched four different variants of a new malware at various Ukrainian targets. Cyber security firms have attributed these attacks to a group known as Armageddon (aka Gamaredon/Shuckworm), which has been linked to Russia’s Federal Security Service (FSB).Footnote 6
Cyber activity against Ukrainian communications
In early March, the Security Service of Ukraine (SBU) reported that cyber threat actors compromised local government and regional authorities’ websites to push disinformation about a Ukrainian surrender and a peace treaty signed with Russia. Footnote 7
In early March, the connection to and from SpaceX’s Starlink satellite internet terminals, which were providing supplemental internet access to the Ukrainian government, were jammed for several hours at a time, likely by Russian-aligned threat actors. Starlink revised their software and the jamming has not resumed.Footnote 8
In late March, suspected Russia-aligned threat actors caused a major disruption of Ukrtelecom, a Ukrainian internet provider, causing one of the most widespread internet outages in the country since the start of the invasion. Footnote 9
In late April, the Computer Emergency Response Team of Ukraine (CERT-UA) warned of ongoing DDoS attacks targeting pro-Ukraine sites and the government web portal through compromised WordPress sites.Footnote 10
Cyber activity against the Ukrainian energy sector
In early April, Russian military intelligence (GRU) cyber threat actors Sandworm tried to deploy the Industroyer2 malware and several destructive malware families against high-voltage electrical substations in Ukraine to cause widespread power outages.Footnote 11 The Sandworm actors were able to move from the victim’s information technology (IT) network to its industrial control system (ICS) network. CERT-UA, working with Slovak internet security company ESET, were able to remediate and protect the targeted network.Footnote 12
Cyber activity against the Ukrainian government
In May 2022, the Russian hacktivist group XakNet claimed to have breached the Ukrainian Ministry of Foreign Affairs, releasing exfiltrated documents on their social media channel through a hack and leak operation.Footnote 13 The XakNet team offered a bounty to their approximately 20,000 subscribers with rewards for the most competent analyses of the data.
Russia-linked cyber actors have repeatedly targeted various Ukrainian government departments with DDoS attacks and various types of wiper malware.Footnote 14
Timeline on military attacks and cyber operations in Ukraine: February 14 to May 16 Footnote 15
Examples of kinetic activity and significant Russian cyber activity.
February 2022
Kinetic activity
-
February 24
Russian tanks advance into Sumy city centre
Significant Russian cyber activity
-
February 14
Odessa-based critical infrastructure compromised by likely Russian actors -
February 17
Suspected Russian actors present on critical infrastructure networks in Sumy -
February 24
Russian actors disrupt the majority of the European KA-SAT communications network -
February 28
Threat actor compromises a Kyiv-based media company
March 2022
Kinetic activity
-
March 1
Missile strikes Kyiv TV tower -
March 3
Widespread electricity outages in Sumy, including blasts at power stations -
March 3
Russia’s military occupies Ukraine’s largest nuclear power station -
March 6
Russian forces launch eight missiles at Vinnytsia airport -
March 11
First Russian strikes in Dnipro hit government buildings -
March 16
Russian rockets strike TV tower in Vinnytsia
Significant Russian cyber activity
-
March 1
Kyiv-based media companies face destructive attacks and data exfiltration -
March 2
Russian group moves laterally on network of Ukrainian nuclear power company -
March 4
APT28 compromises government network in Vinnytsia -
March 11
Dnipro government agency targeted with destructive implant -
March 28
Cyber attack on Ukrainian telecom company causes widespread outages
April 2022
Kinetic activity
-
April 3
Russian airstrikes hit fuel depots and processing plants around Odessa -
April 8
Russian missiles strike Kramatorsk railway station -
April 10
Russian shelling destroys Dnipro International Airport -
April 19
Russia launches simultaneous missile attacks directed at Kyiv and Lviv
Significant Russian cyber activity
-
April 8
Sandworm targets Ukrainian power grid -
April 22
Ukraine’s national postal service hit by a DDoS attack
May 2022
Kinetic activity
-
May 16
Russian forces gain full control of Mariupol
Significant Russian cyber activity
Data collection for this timeline ended May 16. Cyber activity is ongoing
Notable Russian and Russia-linked cyber activity beyond Ukraine
While Russian cyber threat activity in relation to the war in Ukraine has been predominantly focused on Ukrainian targets, several incidents have spilled over into other countries, and the threat of spillover effects from Russian cyber operations remains a pressing concern for the international community.
For example, beginning on February 24, 2022, Russian cyber threat actors carried out an operation that disrupted the majority of Viasat’s European KA-SAT satellite communications service network, with the intended purpose to disrupt the communications capability of the Ukrainian military. Footnote 16 As of March 10, thousands of KA-SAT satellite network modems were rendered inoperable, including modems located in France, Germany, Greece, Hungary, Italy, and Poland. On May 10, 2022, Canada and FVEY allies, as well as the EU and Ukraine, publicly attributed this attack to the Russian government. Footnote 17
Between April 15-22, a pro-Russia hacking group, Killnet, claimed responsibility for over 20 DDoS attacks across multiple critical infrastructure sectors in Czechia, Estonia, Latvia, Poland, the UK, and the US. Footnote 18
Targeting the EU and NATO
We assess that Russian state-sponsored cyber threat actors have almost certainly increased cyberespionage targeting of NATO countries in response to NATO’s support for Ukraine. Since January 2022, Russian cyber actors have targeted government, academic, private sector, and critical infrastructure entities in Denmark, Latvia, Lithuania, Norway, Poland, the US, and Turkey for cyberespionage purposes, as well as entities in Finland and Sweden, both of whom applied for NATO membership following the Russian invasion of Ukraine in February.Footnote 19
In early April, Ukrainian authorities publicly reported several spear-phishing attempts attributed to FSB cyber actors targeting Ukrainian and unspecified EU government targets. Footnote 20
In late April, a previously unknown and financially motivated hacking group (Hive0117) dropped a copy of DarkWatchman malware in a phishing campaign impersonating a Russian agency and targeting Eastern European countries.Footnote 21
In mid-May, an unknown threat actor targeted German users interested in the Ukraine crisis by using a decoy site to lure users into downloading malicious documents, which infected them with a custom PowerShell remote access Trojan (RAT) and stole data.Footnote 22
We assess that Russia is almost certainly in the process of developing cyber capabilities against targets in the EU and NATO, including the US and Canada.Footnote 23
In Canada
From as early as January 2022, evolving intelligence indicates that Russian cyber threat actors are exploring options for potential counterattacks against the United States, Canada, and other NATO/Five Eye allies, including against critical infrastructure.Footnote 24 Russian state-sponsored threat actors have already demonstrated the ability to disrupt critical industrial control systems (ICS) through destructive malware. In addition, some pro-Russian cyber actors have threatened to conduct cyber operations against countries/organizations providing material support to Ukraine.Footnote 25
Non-state actors targeting Russia
In response to a barrage of Russia-linked cyberattacks against Ukraine leading up to and during the invasion, several non-state cyber threat actors came out in support of Ukraine, including by answering the Ukrainian government’s call on volunteer hackers to take down Russia’s websites.Footnote 26
Hacktivist collective Anonymous–affiliated hacker YourAnonSpider claimed responsibility for the RuTube hack in early May that took down Russia’s video platform for at least two days.Footnote 27 At around the same time, Anonymous-affiliated group NB65 took credit for breaching the servers of several major Russian television networks and taking them offline.Footnote 28
In March and April, hackers claimed to have breached dozens of Russian businesses and institutions, including one of Russia’s primary intelligence services. Anonymous and Network Battalion 65, in collaboration with the transparency collective Distributed Denial of Secrets, claimed responsibility for many of these operations. In mid-June, Anonymous claimed to have hacked Russia’s unmanned aerial vehicle (UAV) plans.Footnote 29
Key players engaged in this cyber activity
We assess that the scope and severity of cyber operations related to the Russian invasion of Ukraine has almost certainly been more sophisticated and widespread than has been reported in open sources. Cyber operations have been conducted by threat actors supporting both Russia and Ukraine.
Russian state-sponsored cyber threat actors
Cyber threat activity against Ukraine has been conducted by various actors linked to the three main Russian intelligence services – the FSB, Foreign Intelligence Service (SVR), and GRU. These cyber actors have been involved in various types of threat activity against Ukraine, including both disruptive and destructive cyber operations. Footnote 30
Pro-Russia cyber threat actors
GHOSTWRITER/UNC1151 is a long-running collection of online foreign influence activities—reportedly associated with the governments of Russia and Belarus. Their activities include disinformation, credential harvesting, hack and leak operations, espionage, and false flag operations.Footnote 31
Cybercriminals and hacktivists
Supporting Russia:
- some Russian-speaking cybercrime groups have publicly declared their support for Russia’s invasion of Ukraine. For example, the Conti ransomware group threatened to retaliate against anyone who conducts computer network attacks on Russian critical infrastructure.Footnote 32 Before its recent rebranding and reorganization, Conti was the most impactful ransomware group affecting Canada.
- Beregini is a pro-Russia hacker group based in Ukraine consistently targeting the Ukrainian Government and military.Footnote 33 Russian hacktivist group XakNet Team has also targeted Ukraine Footnote 34.
- Killnet, a pro-Russia hacking group, has been conducting a large number of DDoS attacks against websites of countries providing support to Ukraine, especially websites linked to critical infrastructure such as transport. Most recently, on May 11, 2022, Killnet targeted Italy’s Defense Ministry, Senate, and National Health Institute. Footnote 35
- Cooming project is another ransomware group that declared its support for the Russian government Footnote 36.
Supporting Ukraine:
- As noted above, members of the hacktivist collective Anonymous have launched various cyber operations against the Russian government and Russian industrial firms, including leaking data, wiping files, DDoS operations, and hacking into Russian state television.Footnote 37Another hacking group, the Belarusian Cyber Partisans, have also focused on breaching Russian targets, though their impact to date has been limited Footnote 38.
- According to Ukrainian officials, more than 400,000 people have volunteered to help a crowdsourced Ukrainian government effort (“IT army”) to protect Ukrainian networks Footnote 39.
Key indicators associated with cyber scenarios
CSE monitors both classified and unclassified sources of information to determine the strategic intent of cyber threat actors. As Russian cyber activity is rooted in the Russian government’s stated policy goals, CSE also monitors classified and open-source reporting on domestic developments in Russia.
While it is difficult to predict future cyber activity, indicators that we are tracking include:
Contextual indicators
- an intensification of the conflict in Ukraine, or continued Russian setbacks
- continued or reinforced NATO support for the conflict
- continued or intensified economic sanctions or new measures against Russia
- increasingly aggressive rhetoric from the Russian government
- declarations of red lines
- drastic decline in Russian domestic support
- declarations of specific support to Russia by other state/non-state actors
Cyber activity indicators
- increased cyber targeting of Canada’s allies, particularly the United States
- increased volume of reconnaissance or scanning activity targeting Canadian/allied government, military, civilian targets
- increased volume of compromises or attempts to compromise Canadian/allied government, military, civilian targets
- increased interest in and testing of capability against specific technologies used in critical infrastructure sectors (i.e., ICS devices, uninterruptible power supply (UPS), human-machine interface systems)
- increased instances of pre-positioning in critical infrastructure networks (i.e., finance, energy, utilities)
- specific targeting of individuals/entities involved in, or related to, sanctions
Mitigating risk, raising awareness, and increasing cyber security
Since mid-January, the Cyber Centre has reached out to all Canadian critical infrastructure sectors to reinforce the need to enhance vigilance and follow Cyber Centre advice regarding Russian cyber threat tactics, techniques, and procedures. The Cyber Centre has shared information publicly wherever possible, and through trusted channels for more sensitive technical indicators and advice related to the current crisis.
Allied and Cyber Centre warning products released
Beginning in 2021, during Russia’s military buildup along the Ukrainian border, and throughout 2022, following Russia’s unjustifiable and unprovoked invasion of Ukraine, the Cyber Centre has been monitoring the evolving threat landscape and its impacts—both intentional and spillover—on Canadians and Canadian organizations. Throughout this time period, the Cyber Centre has released eight products to advise, alert, and inform on the threats and possible impacts stemming from the Russian invasion of Ukraine:
Alerts
- AL22-001 – Wiper malware targeting Ukrainian organizations
(January 17, 2022) - AL22-002 – Disruptive activity against Ukrainian organizations - Update 1
(February 24, 2022)
Joint cyber security advisories
- Joint cyber security advisory on weak security controls and practices routinely exploited for initial access
(May 17, 2022) - Joint cyber security advisory on protecting against cyber threats to managed service providers and their customers (May 11, 2022)
- Joint cyber security advisory on 2021 top routinely exploited vulnerabilities
(April 27, 2022) - Joint cyber security advisory on Russian state-sponsored and criminal cyber threats to critical infrastructure
(April 20, 2022)
Cyber threat bulletins
- Cyber Centre reminds Canadian critical infrastructure operators to raise awareness and take mitigations against known Russian-backed cyber threat activity
(February 13, 2022) - Cyber Centre urges Canadian critical infrastructure operators to raise awareness and take mitigations against known Russian-backed cyber threat activity
(January 1, 2022)
CSE alerting Canadians on Russian disinformation activity
In addition to destructive cyberattacks and cyberespionage efforts, Russian state-sponsored and affiliated cyber threat actors are deploying cyber influence operations that are designed to support its war aims. Starting April 1, 2022, CSE declassified intelligence via its social media account to expose some of the disinformation that Russia is spreading about the conflict in Ukraine:
- On April 6, CSE flagged that Russia is claiming that the US is establishing military biological labs in former Soviet countries and that Ukraine is being used as a biological testing ground. Footnote 40
- On April 13, 2022, CSE reported that Russia is spreading disinformation about Canadian Forces members committing war crimes in Ukraine and using doctored images to back up false narratives about Canada’s involvement in the conflict. Footnote 41
- On April 25, CSE reported that Russia was deflecting blame for atrocities committed by Russian forces and was making false claims that Ukraine has breached Geneva conventions, causing dissent within the Ukrainian army. Footnote 42
Lack of incident reporting remains a challenge: We strongly encourage Canadian entities in all critical sectors to report compromises or potential compromises to the Cyber Centre. The Cyber Centre relies on this information to generate a more complete picture of cyber threats faced by Canada and refine advice and guidance to guard against evolving tactics.
- notification, and initial advice and guidance
- mitigation and containment support
- log analysis and malware analysis and
- digital forensics analysis
Call 1-833-CYBER-88 or email contact@cyber.gc.ca to report a compromise or seek guidance.