Alternate format: National Cyber Threat Assessment 2023-2024 (PDF, 4.1 MB)
About the Cyber Centre
The Canadian Centre for Cyber Security (Cyber Centre) is Canada’s technical authority on cyber security. Part of the Communications Security Establishment (CSE), we are the single unified source of expert advice, guidance, services and support on cyber security for Canadians and Canadian organizations.
The Cyber Centre works in close collaboration with Government of Canada departments, critical infrastructure, Canadian businesses and international partners to prepare for, respond to, mitigate and recover from cyber events. The Cyber Centre is outward-facing, welcoming partnerships that help build a stronger, more resilient cyberspace in Canada. In line with the National Cyber Security Strategy, the Cyber Centre represents a more cooperative approach to cyber security in our country.
As trusted experts in cyber security, we help keep Canada and Canadians safe by:

- being a clear, trusted source of relevant cyber security information for Canadians, Canadian businesses, and critical infrastructure owners and operators
- providing tailored cyber security advice and guidance to protect the country’s most important cyber systems
- working side by side with provincial, territorial and municipal governments, and private sector partners to solve Canada’s most complex cyber challenges
- developing and sharing our specialized cyber defence technology and knowledge
- defending cyber systems, including Government of Canada networks, by developing, deploying sophisticated cyber defence tools and technology
- leading the Government’s operational response during cyber events by using our expertise and access to provide information immediately useful for managing incidents
Through our work and partnerships, we help raise Canada’s cyber security bar so Canadians can live and work online safely and with confidence.
Learn more by visiting Cyber.gc.ca or follow us on Twitter @cybercentre_ca.
Table of contents
- About the Cyber Centre
- Minister's foreword
- Message from the Head of the Cyber Centre
- Executive Summary
- About this document
- Introduction – Cyber threats are evolving
- Ransomware is a persistent threat to Canadian organizations
- Critical infrastructure is increasingly at risk from cyber threat activity
- State-sponsored cyber threat activity is impacting Canadians
- Cyber threat actors are attempting to influence Canadians, degrading trust in online spaces
- Disruptive technologies bring new opportunities and new threats
- Conclusion
Minister's foreword
Over the last two years, cyber security has become a top concern for Canadians. Ransomware incidents hit the headlines on an almost daily basis both in Canada and around the world. Our essential services are being disrupted, from hospitals and schools to municipalities and utility providers. Our personal and financial data are being stolen, traded, or leaked online. Our online spaces are being flooded with false information and divisive rhetoric.
The National Cyber Threat Assessment 2023-2024 will help Canadians understand current cyber security trends, and how they are likely to evolve.
The Cyber Centre has provided an overview of the cyber threat landscape that is both thorough and accessible. The NCTA is especially helpful for Canadian decision-makers as the focus is on cyber threats most relevant to Canada. In addition to public reporting, the NCTA also benefits from CSE’s classified sources and from the Cyber Centre’s work defending the Government of Canada from malicious cyber activity day in day out. In short, this information is both credible and comprehensive.
As technology continues to accelerate with rapid speed, threats also continue to evolve. The Cyber Centre is working hard to bolster cyber security capabilities across Canada, in partnership with industry, academia and all levels of government.
It will take a coordinated effort to make Canada one of the safest places to live and work online. The Cyber Centre’s work will protect Canadians and help ensure we are prepared to act, adapt, and react to cyber threats.
The Honourable Anita Anand
Minister of National Defence
Message from the Head of the Cyber Centre
Thank you for making cyber security a priority by reading this report.
If you have read either of our previous National Cyber Threat Assessments, published in 2018 and 2020, much of what you read here will seem familiar.
Cybercrime is still the number one cyber threat activity affecting Canadians. The state-sponsored cyber programs of China, Russia, Iran and North Korea continue to pose the greatest strategic cyber threat to Canada. Critical infrastructure is still a prime target for both cybercriminals and state-sponsored actors alike.
While it may be reassuring to know that our analysis of the key trends holds true, the overall picture of the threat landscape is anything but reassuring. You may be tempted to stop reading halfway through, disconnect all your devices and throw them in the nearest dumpster. Or perhaps, more realistically, to shrug your shoulders in resignation and carry on exactly as before. My hope is that instead, you will see this report as a call to action.
Canadians benefit greatly from living in one of the most Internet-connected nations in the world, and the cyber risks we identify in this report can be mitigated. In fact, the vast majority of cyber incidents can be prevented by basic cyber security measures.
To help bridge the gap between knowledge and action, we have prepared advice and guidance tailored to the five narratives identified in this report. These companion publications outline practical steps to mitigate the risks associated with each theme. Further advice and guidance can be found on the Cyber Centre’s website. And as ever, the Get Cyber Safe website offers a wealth of simple and effective cyber security tips for individual Canadians.
Whether you are new to the topic, or a seasoned expert, I hope you find this report and the accompanying guidance helpful in taking the next step towards better cyber security.
Sami Khoury
Head, Canadian Centre for Cyber Security
Executive summary
Canadians use the Internet for financial transactions, to connect with friends and family, attend medical appointments and work. As Canadians spend more time and do more on the Internet, the opportunities grow for cyber threat activity to impact their daily lives. There’s been a rise in the amount of personal, business and financial data available online, making it a target for cyber threat actors. This trend towards connecting important systems to the Internet increases the threat of service disruption from cyber threat activity. Meanwhile, nation states and cybercriminals are continuing to develop their cyber capabilities. State-sponsored and financially motivated cyber threat activity is increasingly likely to affect Canadians. In NCTA 2023-24, we have chosen to focus on five cyber threat narratives that we judge are the most dynamic and impactful and that will continue to drive cyber threat activity to 2024.
Key judgements
- Ransomware is a persistent threat to Canadian organizations. Cybercrime continues to be the cyber threat activity most likely to affect Canadians and Canadian organizations. Due to its impact on an organization’s ability to function, ransomware is almost certainly the most disruptive form of cybercrime facing Canadians. Cybercriminals deploying ransomware have evolved in a growing and sophisticated cybercrime ecosystem and will continue to adapt to maximize profits.
- Critical infrastructure is increasingly at risk from cyber threat activity. Cybercriminals exploit critical infrastructure because downtime can be harmful to their industrial processes and the customers they serve. State-sponsored actors target critical infrastructure to collect information through espionage, to pre-position in case of future hostilities, and as a form of power projection and intimidation. However, we assess that state-sponsored cyber threat actors will very likely refrain from intentionally disrupting or destroying Canadian critical infrastructure in the absence of direct hostilities.
- State-sponsored cyber threat activity is impacting Canadians. We assess that the state-sponsored cyber programs of China, Russia, Iran, and North Korea pose the greatest strategic cyber threats to Canada. State-sponsored cyber threat activity against Canada is a constant, ongoing threat that is often a subset of larger, global campaigns undertaken by these states. State actors can target diaspora populations and activists in Canada, Canadian organizations and their intellectual property for espionage, and even Canadian individuals and organizations for financial gain.
- Cyber threat actors are attempting to influence Canadians, degrading trust in online spaces. We have observed cyber threat actors’ use of misinformation, disinformation, and malinformation (MDM) evolve over the past two years. Machine-learning enabled technologies are making fake content easier to manufacture and harder to detect. Further, nation states are increasingly willing and able to use MDM to advance their geopolitical interests. We assess that Canadians’ exposure to MDM will almost certainly increase over the next two years.
- Disruptive technologies bring new opportunities and new threats. Digital assets, such as cryptocurrencies and decentralized finance, are both targets and tools for cyber threat actors to enable malicious cyber threat activity. Machine learning has become commonplace in consumer services and data analysis, but cyber threat actors can deceive and exploit this technology. Quantum computing has the potential to threaten our current systems of maintaining trust and confidentiality online. Encrypted information stolen by threat actors today can be held and decrypted when quantum computers become available.
About this document
This document highlights the cyber threats facing individuals and organizations in Canada. It provides an update to the National Cyber Threat Assessment 2018 (NCTA 2018) and the National Cyber Threat Assessment 2020 (NCTA 2020), with analysis of the interim years and forecasts until 2024. We recommend reading the NCTA 2023-24 along with the updated Introduction to the Cyber Threat Environment and the tailored advice and guidance that we have released as companions to this assessment.
As envisioned in the National Cyber Security Strategy, we prepared this document to help Canadians shape and sustain our nation’s cyber resilience. It is only when the government, private sector and public work together that we can build resilience to cyber threats in Canada.
Limitations: This assessment does not provide an exhaustive list of all cyber threat activity in Canada or mitigation advice. As a threat assessment, the purpose of this document is to describe and evaluate the threats facing Canada. We focus on understanding the current cyber threat environment and how threat activity can affect Canadians and Canadian organizations. Cyber security guidance can be found on the Cyber Centre website and on the Get Cyber Safe website.
Sources: The key judgements in this assessment rely on reporting from multiple sources, both classified and unclassified. The judgements are based on the Cyber Centre’s knowledge and expertise in cyber security. Defending the Government of Canada’s information systems provides the Cyber Centre with a unique perspective to observe trends in the cyber threat environment, which also informs our assessment. CSE’s foreign intelligence mandate provides us with valuable insights into adversary behaviour in cyberspace. While we must always protect classified sources and methods, we provide the reader with as much justification as possible for our judgements.
Assessment process: Our cyber threat assessments are based on an analytical process that includes evaluating the quality of available information, exploring alternative explanations, mitigating biases and using probabilistic language. We use the terms “we assess” or “we judge” to convey an analytic assessment. We use qualifiers such as “possibly,” “likely,” and “very likely” to convey probability.
This threat assessment is based on information available as of Tuesday, October 4th, 2022
Note: These percentages are not derived via statistical analysis, but are based on logic, available information, prior judgements and methods that increase the accuracy of estimates.
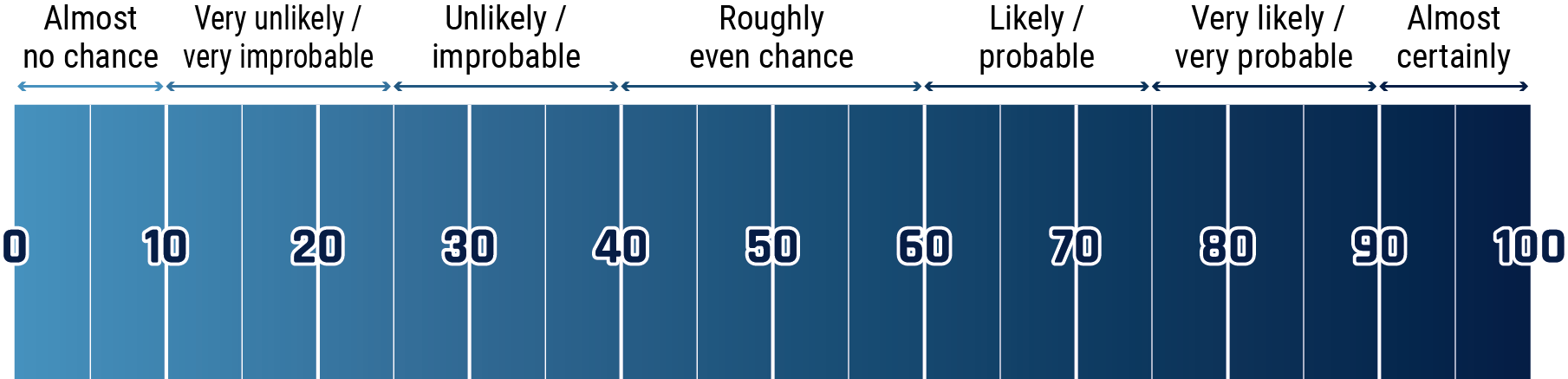
Long description - Estimative language chart
- 1 to 9% Almost no chance
- 10 to 24% Very unlikely/very improbable
- 25 to 39% Unlikely/improbable
- 40 to 59% Roughly even chance
- 60 to 74% Likely/probably
- 75 to 89% Very likely/very probable
- 90 to 99% Almost certainly
Introduction – Cyber threats are evolving
In previous editions of the National Cyber Threat Assessment (NCTA), we outlined the cyber threats faced by Canadian individuals, organizations, and critical infrastructure providers and assessed how they would evolve over the following years. Many of the threats that we identified remain relevant today, but the nature of these threats has changed. Threat actors have adapted their techniques, new technologies have spurred new cyber capabilities, and Canadians are using the Internet more and in novel ways.
COVID-19 and the cyber threat landscape
In 2020, we discussed how the COVID-19 pandemic quickly changed the cyber threat landscape. Over two years after the start of the pandemic, Canadians have a different relationship with the Internet. More people now use the Internet to shop, buy groceries, regularly connect with friends and family, attend medical appointments and work. Today, Canadians are working through a combination of in-person, virtual and hybrid means. Since 2020, more organizations have adopted cloud-based services to work efficiently in a hybrid environment.
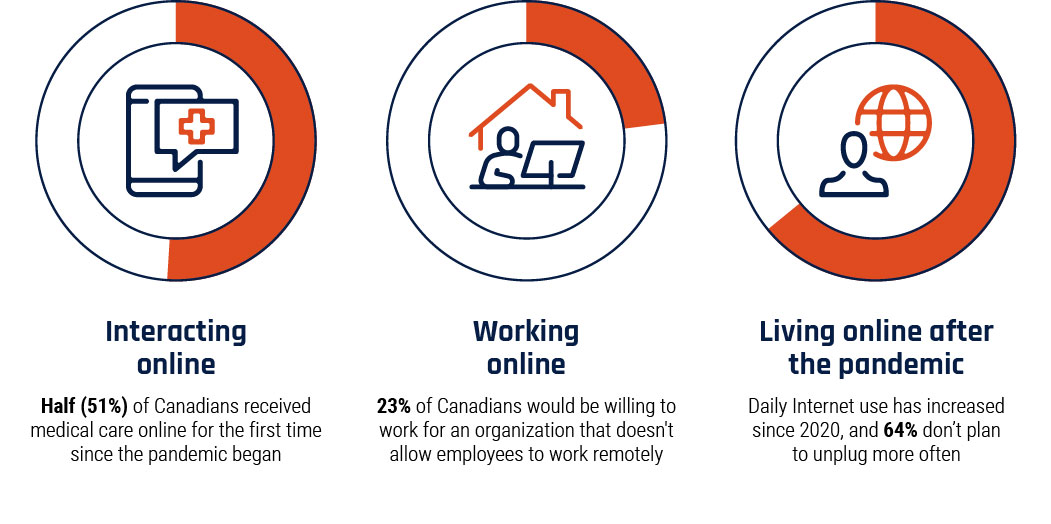
Long description - Figure 1
Graphic depicting the lasting impacts of COVID-19 on how Canadians use the Internet.
- Interacting online: Half (51%) of Canadians received medical care online for the first time since the pandemic began
- Working online: 23% of Canadians would be willing to work for an organization that doesn’t allow employees to work remotely
- Living online after the pandemic: Daily Internet use has increased since 2020, and 64% don’t plan to unplug more often
We judge that the threat surface available to malicious cyber actors has expanded since 2020. The amount of data collected on individual Canadians today is significant. It will only increase as new technologies enter the mainstream, creating a wealth of opportunities for threat actors looking to steal sensitive personal information. Moreover, the global threat landscape is changing as nation states increasingly use cyber activity as a tool for strategic competition and conflict.
To help Canadians gain a deeper understanding of the cyber threat landscape, we have also updated and expanded the Cyber Centre’s Introduction to the Cyber Threat Environment.
In this section we describe the trends driving today’s cyber threat landscape and assess how we expect them to evolve.
Hybrid work and work-from-anywhere broadens the threat surface for individuals and organizations
More than one third of Canadians worked from home more often during the pandemic. Footnote 2 Now, more than two years on, many Canadians are transitioning to a more permanent hybrid work environment. Footnote 3 Securely implemented and maintained work-from-anywhere offers flexibility to employees and their employers, but it also creates a larger threat surface through which threat actors can access organizations’ and individuals’ networks or devices.
Business networks are becoming integrated into employees’ homes and public spaces. We assess that cyber threat actors will very likely continue to exploit hybrid work infrastructure and target employees’ home networks and personal devices to gain access to Canadian organizations. Cyber threat actors are taking advantage of organizations’ remote accessibility, attempting to compromise corporate networks via remote connections. Footnote 4 When employees access corporate networks and information from their home networks and devices, they create opportunities for cyber threat actors to do the same. This allows them to access sensitive business or employee information. Footnote 5
Faster, broader connections and more devices connected to the Internet
More Canadians are using Internet-connected technology for day-to-day interactions
Canadians have become more proficient Internet users, increasingly using the Internet for entertainment, information, work and social interactions. Footnote 6 Canadians are also becoming more widely connected as government initiatives extend reliable high-speed Internet to remote areas and new technologies, such as satellite Internet, ease the geographic element of the digital divide. Footnote 7 The COVID-19 pandemic has underscored the importance of accessible and reliable Internet connections. It made it necessary to move previously physical interactions online and required the quick adoption of technologies related to telework and education, contact tracing, and online retail and banking. The widespread adoption of contactless technologies for Canadians’ day-to-day activities increases their exposure to cyber threat activity, such as data theft, fraud and extortion.
Internet-connected operational technology and smart systems expand the reach of cyber threat activity
The continued trend towards connecting devices that interact with the physical world, including deployment of Internet of Things (IoT) and Industrial IOT (IIoT) devices, are expanding the cyber threat surface. Their use will almost certainly grow as Canada fully adopts fifth generation cellular technology (5G). 5G provides significant improvements over 4G/LTE that will allow more devices to connect at much higher speeds. This has implications for smart cities, precision agriculture and other uses of “smart” systems such as applications that rely on sensors, automation and large amounts of data. Footnote 8 As Canada adopts smart systems and becomes more digitally transformed, more sectors and services will become vulnerable to cyber threat activity. This includes espionage, fraud, extortion and sabotage. Smart systems generate large amounts of data which, in certain applications, may include detailed personal information from users. As smart systems are incorporated into physical services and exposed to the Internet, the potential for service disruption from cyber threat activity increases.
Cybercrime represents a sophisticated threat to Canada
As we assessed in previous NCTAs, cybercrime remains the cyber threat that is most likely to affect Canadians. This is in part driven by a flourishing market for cybercrime tools and services readily available via online marketplaces and forums, or in private cybercrime communities. Such tools and services include initial network access, distributed denial of service (DDoS) attacks, web defacement tools, malware (including ransomware) and money laundering technologies. This allows cybercriminals to purchase specialized capabilities instead of developing their own skills over time. This lowers the barrier to entry for cybercriminals, enabling even unsophisticated threat actors to take advantage of more effective and specialized tools and services.
The availability and ease of access to leaked and stolen information like login credentials, financial information and personal information continues to grow on cybercrime forums. Footnote 9 This stolen data enables further cybercrime, including fraud, scams, and more disruptive cyber activity like ransomware. Ransomware is one of the most impactful cyber threats in Canada, benefiting significantly from the specialized cybercrime economy and the growing availability of stolen information. Cybercriminals leverage cryptocurrencies, use encrypted communications to maintain their anonymity and evade enforcement activity. Footnote 10 Cybercriminals are also quick to adopt and manipulate new technologies for their own gain. For example, cybercriminals have leveraged decentralized finance, which uses cryptocurrencies to enable large-scale borrowing and lending of funds without intermediaries, to steal large sums of money. Footnote 11 The significant payouts of cybercrime, including from ransomware and from fraud and scams such as business email compromise (BEC), will very likely continue to attract interest from new groups of criminal actors even as others are constrained by increased law enforcement activity.
Threat actors are attacking targets indirectly, exploiting vulnerabilities in supply chain and Internet infrastructure
Instead of targeting organizations directly, cyber threat actors are increasingly targeting the software tools and services used by organizations via supply chain compromises. The threat from supply chain compromises increases where vendors have elevated access to their clients’ networks. This kind of relationship is becoming more common as cloud-based software, infrastructure, and platform “as-a-service” models proliferate. By spreading malware through a vendor’s updates and services, cyber threat actors introduce vulnerabilities on the vendor’s clients’ networks. Supply chain compromises tend to be more complex than direct compromises. As such, we assess they will very likely remain a tool primarily for state-sponsored threat actors and sophisticated cybercriminals.
Cyber threat actors are also exploiting weaknesses in code that is widely used across the Internet and in software development. Web services and computer applications often rely on open-source code maintained by third parties. When vulnerabilities are found in common third-party code, any project using that code is vulnerable. For applications such as Log4J, a popular open-source software with a vulnerability disclosed in late 2021 and exploited widely by cyber threat actors, the impact can be pervasive. Footnote 12 In just the four months prior to the exploit becoming widely known, Log4J was downloaded over 28 million times. Footnote 13 The exploit, Log4Shell, was made publicly available, providing cyber threat actors broad access to the tools to compromise any service using Log4J. Footnote 14
We assess that vulnerabilities in common services and software components will almost certainly continue to be discovered and exploited by threat actors at scale. We also assess that, even after patches are developed, threat actors will almost certainly continue to scan the Internet to opportunistically target unpatched systems.
Russia’s invasion of Ukraine – A new perspective on cyber
Russia’s invasion of Ukraine in February of 2022 gave the world a new understanding of how cyber activity is used to support wartime operations. Russian-sponsored malicious cyber activity against Ukraine has disrupted or attempted to disrupt organizations in government, finance and energy, often coinciding with conventional military operations. These attacks have expanded beyond Ukraine to implicate European critical infrastructure as well. For example, Russia’s attack on a European satellite Internet provider that resulted in a significant outage in several European countries. Footnote 16 Cyber and military activities have also been supported by coordinated disinformation operations to support Russia’s narrative about the invasion. Footnote 17
Geopolitical competition in cyberspace puts everyone at risk
Nation states use malicious cyber activity as a tactic for subversion and power projection to achieve their geopolitical goals. Malicious cyber threat activity by state-sponsored cyber threat actors has become an important tool for states to influence events without reaching the threshold of conflict and to support conventional warfare.
Canadian critical infrastructure is almost certainly targeted by malicious cyber activity from nation state-backed cyber actors. While we maintain that state-sponsored cyber threat actors will very likely refrain from intentionally disrupting or destroying Canadian critical infrastructure in the absence of direct hostilities, these actors are developing the ability to disrupt the critical systems of Canada and our allies. If carried out, this activity can have significant implications for Canadians’ ability to communicate and receive essential goods and services. Likewise, state-sponsored cyber threat actors proliferate misinformation, disinformation, and malinformation (MDM) to influence international populations and exploit social divisions. Footnote 15 This activity serves to justify or build support for states’ ideological goals, impact international discourse related to current events, or build mistrust to weaken Canadian democratic institutions.
The global Internet continues to diverge
In NCTA 2020, we described how nation states are developing competing standards and norms governing the flow of information on the Internet. One approach, which focuses on state sovereignty, sees online information primarily through the lens of stability and national security and promotes an Internet that will allow states to track their citizens and censor information. Using the Internet to censor and monitor populations threatens the openness, transparency, and multi-stakeholder approach to the Internet that Canada and its allies champion. Yet, an increasing number of states are managing their domestic Internet in this way. In 2021, AccessNow reported that 34 countries used Internet shutdowns as a tool to suppress social or political unrest or control the flow of information during elections and in conflict. Footnote 18 Freedom House estimates that 56% of the world’s Internet users live in countries where political, social, or religious content was blocked online. Footnote 19
Over the next two years, it is very likely that the divergence between an open and transparent Internet and an Internet based on state sovereignty will continue to grow. Russia and China have invested in their own Internet infrastructure and, alongside other states, are advocating for information and communications technology standards. These would allow more state-led control of the Internet in their respective countries. Footnote 20 In 2022, China introduced a new international organization evolving from the World Internet Conference dedicated to Internet governance and comprised of members from 20 countries. Footnote 21 While Internet governance may appear abstract and quite removed from daily life, we judge that competing technological ecosystems and disparate information environments inhibit the free flow of information, build distrust, and make it more difficult to combat misinformation and disinformation.
Ransomware is a persistent threat to Canadian organizations

As we assessed in previous NCTAs, cybercrime continues to be the cyber threat activity most likely to affect Canadians and Canadian organizations. Fraud and scams are almost certainly the most common form of cybercrime that Canadians will experience over the next two years as threat actors attempt to steal personal, financial, and corporate information via the Internet. Fraud and scams, including malicious cyber threat activity such as phishing, result in significant financial losses. According to the Canadian Anti-Fraud Centre, there have been over 150,000 reports of fraud in Canada with over $600 million stolen since January 2021. Footnote 22
Due to its impact on an organization’s ability to function, ransomware is almost certainly the most disruptive form of cybercrime facing Canadians. Aside from the financial cost of the ransom itself, ransomware can stop the operation of important systems, damage or destroy an organization’s data, and reveal sensitive information. This is in addition to imposing costs and time to recover from an attack. The disruption caused by a ransomware attack can prevent access to essential services and, in some cases, threaten Canadians’ physical safety.
Ransomware almost certainly has more impact on Canadian organizations today than it did in 2020. Since 2020, the frequency of ransomware attacks worldwide has increased, and payment demands against large organizations have grown. Footnote 23
Ransomware enables other malicious cyber threat activity
Ransomware is malicious software that restricts access to or operation of a computer or device, potentially restoring it following payment. Typically, threat actors will compromise a victim, encrypt their data, and demand a ransom to provide a decryption key. Today, most ransomware attacks are double extortion attacks. This means that ransomware actors will exfiltrate files before encrypting them and threaten to leak sensitive information publicly if the ransom is not paid. Footnote 24
Beyond the impact of ransomware itself, data stolen during a ransomware attack almost certainly enables further cyber threat activity from a range of actors. Leaked information often contains sensitive personal and business information that can be accessed freely on the ransomware actors’ websites or sold to a buyer, either privately or on online cybercrime marketplaces. Footnote 25 Other threat actors can use this information to enable further cybercrime activity, such as identity fraud against individuals or even additional ransomware. Threat actors can also leverage sensitive business information to support commercial espionage. In May 2022, a Canadian defence company confirmed in media reporting that it was investigating a possible ransomware incident. Footnote 26 Given the sensitive nature of the organization’s data, this information would likely be of interest to other threat actors for espionage or to enable further cybercriminal activity.
Ransomware affects critical infrastructure
Critical infrastructure is a particularly attractive target for ransomware. As we note when discussing threats to critical infrastructure, these organizations are perceived by cybercriminals to be more willing to pay significant ransoms to limit or avoid physical disruption and impacts to their customers. Ransomware incidents in May 2021 against Colonial Pipeline in the United States (US) and the North American and Australian operations of JBS Foods resulted in multimillion-dollar payouts for threat actors. These incidents caused significant disruptions to fuel and food supply chains. Footnote 27 In Canada, a ransomware attack resulted in a loss of essential services at an Ontario hospital in June 2021. In October 2021, due to some of their servers being encrypted and locked, a municipal transit service was unable to share route and scheduling information. Footnote 28 The Cyber Centre is aware of reported ransomware activity against several industries in Canada since 2020, including most of Canada’s critical infrastructure sectors. While critical infrastructure and large enterprises are attractive targets, cybercriminals are opportunistic and will almost certainly not limit their activities to those sectors in Canada over the next two years.
The impact of ransomware
Cyber security reporting indicates that ransom payments have increased since 2020, likely driven in part by increasingly significant demands against large enterprises. Footnote 29 Even if victims choose to pay the ransom, there are no guarantees that their data will be recovered. One survey of Canadian businesses found that only 42% of organizations who paid the ransom had their data completely restored. Footnote 30 The ransom value often represents only a portion of the total cost to the organization. Lost value associated with downtime or unrecoverable data, costs of repairing systems, and reputational damage are just some of the additional costs that can be imposed by ransomware.
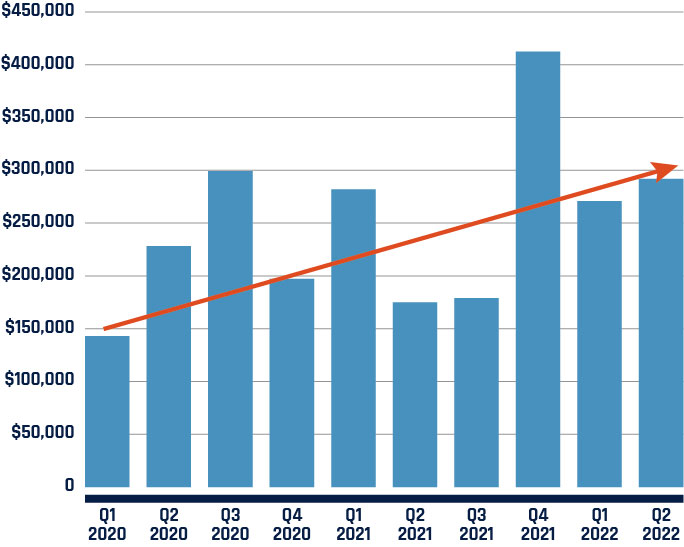
Long description - Figure 2
Bar chart showing the increase in average ransomware payments over time, in Canadian Dollars. Values as follows:
- Quarter 1, 2020 : $146,159
- Quarter 2, 2020 : $233,444
- Quarter 3, 2020 : $306,210
- Quarter 4, 2020 : $201,822
- Quarter 1, 2021 : $288,505
- Quarter 2, 2021 : $178,861
- Quarter 3, 2021 : $183,004
- Quarter 4, 2021 : $421,916
- Quarter 1, 2022 : $277,021
- Quarter 2, 2022 : $298,755
Law enforcement action against cybercriminals using ransomware
In May 2021 and again in early 2022, the Cyber Centre observed a decrease of ransomware incidents against Canadians. We assess this was likely a result of threat actors seeking to avoid law enforcement attention directly following international action.
While law enforcement action almost certainly disrupts cybercriminal operations, we judge that these disruptions rarely have an enduring effect on the ransomware environment. Weeks after Russia’s arrest of 14 individuals associated with a prominent ransomware gang in early 2022, cyber security researchers observed the ransomware group back up in operation. Footnote 32
Ransomware-as-a-service has made ransomware more accessible and profitable
Much of the ransomware affecting Canadians is very likely owned by ransomware-as-a-service (RaaS) cybercrime groups. These groups create and maintain ransomware variants and sell access to other cybercriminals who deploy the ransomware against a victim. Ransomware-as-a-service groups request upfront payment, subscription fees, a cut of profits, or all three in exchange for access to their ransomware. Footnote 33 We judge that this service model lowers the barrier to entry for cybercriminals, making it easier for less-sophisticated cyber threat actors to access ransomware capabilities and extort victims.
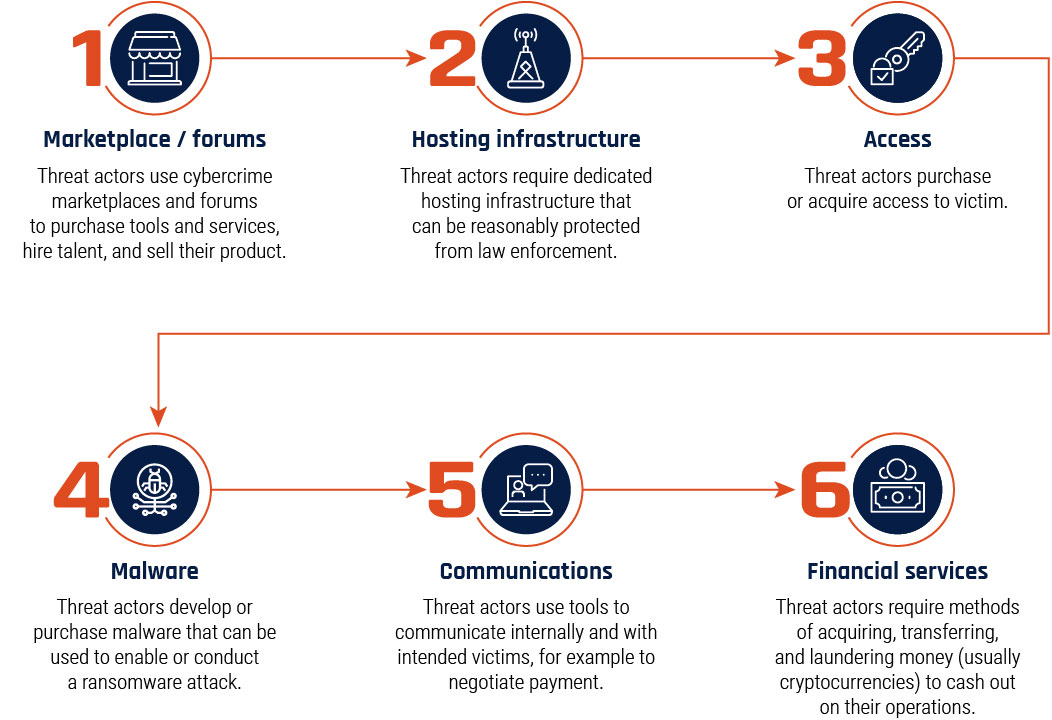
Long description - Figure 3
Visual representation of the cybercriminal ransomware-as-a-service supply chain. Each part of the supply chain has a brief description.
- Marketplaces and forums: Threat actors use cybercrime marketplaces and forums to purchase tools and services, hire talent, and sell their product.
- Hosting infrastructure: Threat actors require dedicated hosting infrastructure that can be reasonably protected from law enforcement.
- Access: Threat actors purchase or acquire access to the victim.
- Malware: Threat actors develop or purchase malware that can be used to enable or conduct a ransomware attack.
- Communications: Threat actors use tools to communicate internally and with intended victims, for example to negotiate payment.
- Financial Services: Threat actors require methods of acquiring transferring, and laundering money (usually cryptocurrencies) to cash out on their operations.
Cybercriminals will continue to adapt their methods to maximize profits
So long as ransomware remains profitable, we will almost certainly continue to see cybercriminals deploying it. A combination of permissive state attitudes, particularly in Russia, towards cybercrime that targets victims outside of the Former Soviet Union countries and an available talent pool of cybercriminals facilitates the growth and development of criminal organizations dedicated to developing and deploying ransomware. Cyber threat actors also demonstrate flexibility and leverage the ransomware supply chain in new ways to ensure that their operations remain feasible. For example, media and vendor reporting indicates that some ransomware operators are transitioning to using privacy coins (cryptocurrencies that provide higher levels of anonymity) to hide their activity more effectively, although Bitcoin remains the most common ransomware payment method. Footnote 34
Targeting supply chains and Managed Service Providers
Cybercriminals will almost certainly continue to target Managed Service Providers (MSP), companies that host and manage their clients’ IT resources, and software supply chains to maximize the reach of ransomware operations. In 2021, media reports indicated that cybercriminals compromised and spread ransomware via Kaseya’s Virtual System Administrator, a system used by MSPs to manage their clients’ networks. Cybercriminals were able to distribute the ransomware to approximately 60 MSPs and 1,500 of their clients. Footnote 35
Methods of extortion are evolving
We assess that over the next two years, cyber threat actors will very likely use a variety of extortion techniques against their victims to maximize their chance of receiving payment. Beyond encrypting systems and stealing data, in some instances ransomware operators will likely use additional techniques, such as threatening an organization’s partners or clients and distributed denial of service (DDoS). By threatening the business partners or clients of a victim, cybercriminals very likely anticipate that these organizations will increase pressure on the victim to pay the ransom, fearing that their sensitive business information or operations are in the hands of the threat actor. Footnote 36 DDoS places additional pressure on a victim by adding another layer of disruption to the organization’s network. One cybercriminal group, which has targeted victims in Canada, has conducted DDoS attacks during payment negotiations. Footnote 37 While multiple extortion attacks are common, some cyber threat actors are moving away from the traditional encryption of victims’ systems to focus solely on other single-extortion methods. Footnote 38
Figure 4: Ransomware extortion methods
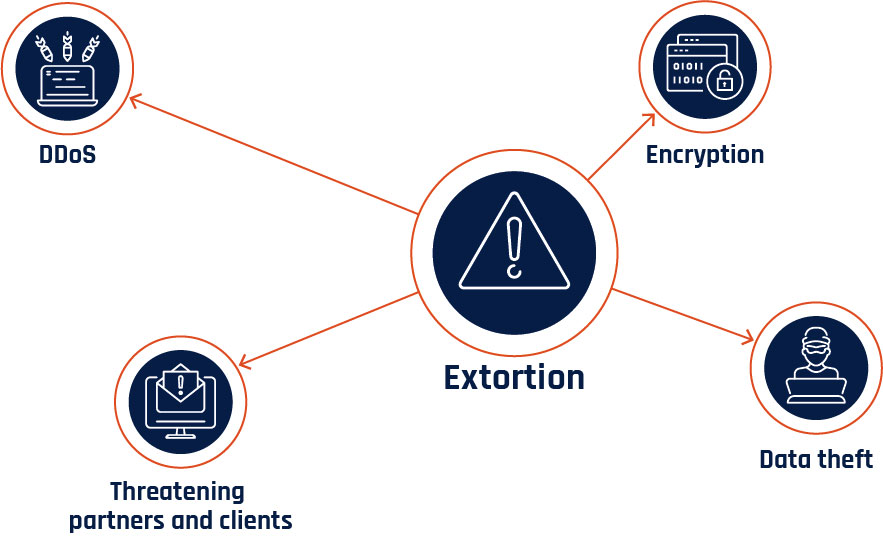
Long description - Figure 4
Graphic depicting common extortion methods:
- Encryption
- Data theft
- DDoS
- Threatening partners and clients
Critical infrastructure is increasingly at risk from cyber threat activity

Critical infrastructure underpins many of the services Canadians use every day. When service interruptions occur, the impacts can be significant. While not linked to malicious cyber activity, cellular and Internet outages in Canada in 2021 and 2022 illustrated the importance of connectivity and the interconnectedness between critical infrastructure sectors. Footnote 39 In addition to the impacts to individuals, the outages impacted payment processing and emergency safety lines. Footnote 40 The opportunities for critical infrastructure disruption expand as operators increasingly expose the operational technology (OT) underpinning industrial processes to the Internet. Internet-connected OT increases the threat surface of the organizations that employ it and increases the opportunity for cyber threat activity to have effects in the physical world.
Cyber threat actors are aware of the impact targeting critical infrastructure can have, exploiting their sensitivity to service interruptions to extort them for ransom. State-sponsored cyber threat actors target critical infrastructure to collect information through espionage, pre-position in case of future hostilities, and as a form of power projection and intimidation. However, we assess that state-sponsored cyber threat actors will very likely refrain from intentionally disrupting or destroying Canadian critical infrastructure in the absence of direct hostilities.
Critical infrastructure providers house large amounts of sensitive or valuable information that can be targeted by cyber threat actors, including intellectual property on the design and maintenance of OT and personal information the provider may have collected from consumers. Sensitive information may also be revealed incidental to financially motivated cyber threat activity. Researchers suggest nearly 1 in 7 ransomware attacks against critical infrastructure where information is stolen and released reveals sensitive information about OT. Footnote 41 Technical information on OT can be used by threat actors to plan future threat activity or can be valuable for sale or as a target for commercial espionage.
Long description - Figure 5
Critical infrastructure sectors:
- Energy and utilities
- Finance
- Food
- Health
- Government
- Safety
- Water
- Transportation
- Information and communication technology
- Manufacturing
Connected OT increases critical infrastructure’s cyber threat surface
In NCTA 2020, we described how OT, which is used to control and monitor physical processes, is increasingly being connected to information technology (IT) by industry and critical infrastructure providers. Connected, or smart, OT increases process efficiency through improved data exchange, centralized management, and automation. The global market for smart OT in 2020 was about $280.05 billion CAD and is expected to grow to over $1 trillion CAD in the early 2030s. Footnote 43 This is in addition to the overall trend towards digitization across all industries to account for the challenges of the COVID-19 pandemic. Footnote 44 The adoption of connected OT has been accelerated by improvements in technology making it even easier to connect devices remotely and at scale, including 5G and satellite Internet infrastructure. While connecting OT brings many benefits, it also increases critical infrastructure providers’ vulnerability to cyber threat activity.
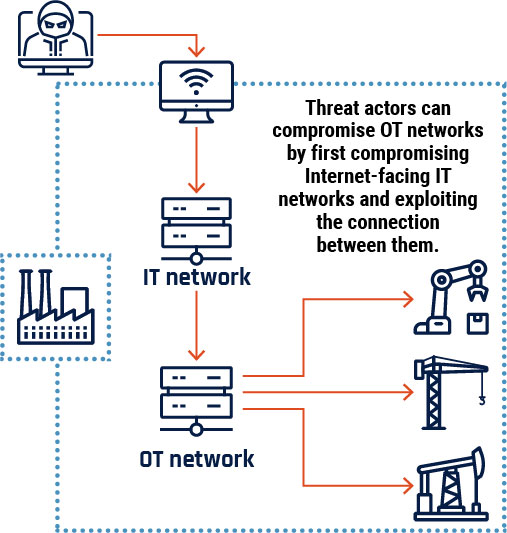
Long description - Figure 6
Graphic depicting how a cyber threat actor can compromise operational technology networks that have been connected to an organization’s information technology network. The Internet-connected information technology network is compromised, and the threat actor uses the link to the operational technology network to access operational technology devices that would otherwise be inaccessible.
Connecting OT to an Internet-connected IT network provides a pathway for threat actors to access and disrupt sensitive OT devices and processes. Threat activity against the IT network can have incidental effects on the OT network. Operators may shut down OT processes out of caution, or IT malware may accidentally spread and affect OT. Footnote 45 We are also observing an increase in use of malware that directly targets and disables OT. Cybercriminals have deployed OT-specific ransomware, and state-sponsored actors have demonstrated the capacity to deploy malware against critical infrastructure to degrade its performance and damage OT and IT assets. Footnote 46 Russian state-sponsored threat actors have been particularly active in developing and testing these capabilities against their neighbours, including against NATO member states. Footnote 47
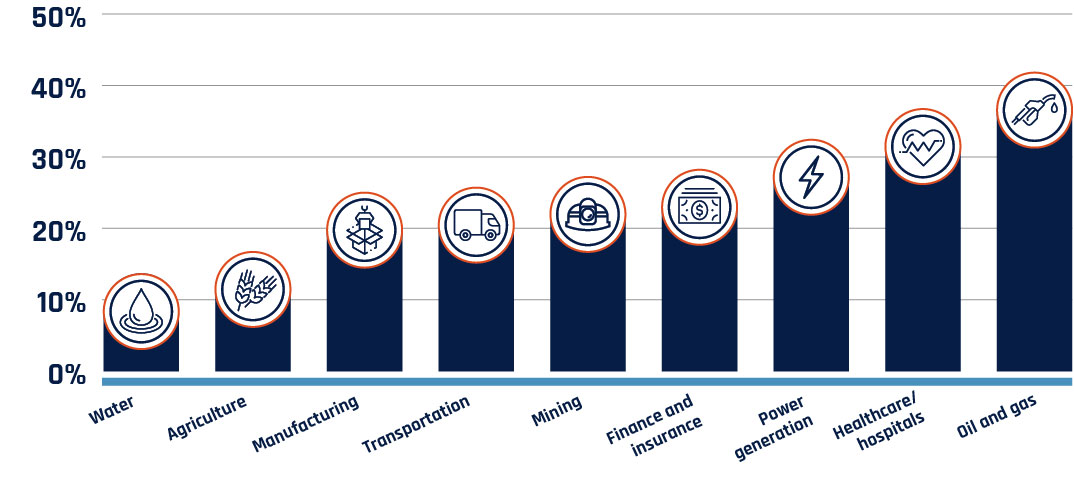
Long description - Figure 7
Horizontal bar chart showing the percentage of critical infrastructure sectors reporting a cyber incident in 2019.
- Oil and gas: 41.8%
- Healthcare – hospitals: 36.7%
- Power generation: 32.4%
- Finance and insurance: 28.2%
- Mining: 27.2%
- Transportation: 25.7%
- Manufacturing: 25%
- Agriculture: 16.7%
- Water: 13.7%
Critical infrastructure depends on its supply chain
Critical infrastructure providers, especially energy and utilities, are reliant on their vendors and suppliers for expertise and equipment as they operate, maintain, and modernize their OT processes. We assess that this makes them particularly vulnerable to supply chain compromises, where cyber threat actors first compromise a vendor and use that access to compromise one or more of their clients. Cyber threat actors target critical infrastructure supply chains for two purposes: to steal intellectual property and information about the OT deployed by a critical infrastructure provider and to obtain indirect access to networks.
Cybercriminals target critical infrastructure
Financially motivated cyber threat actors, predominantly cybercriminals, exploit critical infrastructure because downtime can be harmful to their industrial processes and the customers they serve. Cybercriminal activity against critical infrastructure can interrupt operations that support essential services, utilities, and the production of important goods, including food, fuel and medical equipment in support of their extortion demands.
For the healthcare sector in particular, the impacts of cybercriminal activity can be significant. Footnote 49 Since March 2020, over 400 healthcare organizations in Canada and the United States experienced a ransomware attack. Footnote 50 In 2021, a cyber incident heavily impacted Newfoundland and Labrador’s healthcare system, disrupting medical services in their entire Eastern Health region. Footnote 51
Newfoundland and Labrador healthcare compromise
The Newfoundland and Labrador healthcare system was paralyzed on October 30, 2021, when cybercriminals compromised its networks. Healthcare providers could not access internal communications or diagnostic information, forcing them to adopt a paper-based approach to appointments and emergency procedures. Thousands of medical procedures and appointments were delayed. In addition to service disruptions, sensitive information pertaining to thousands of staff and patients was stolen. Footnote 52
We have also observed an increase in threat activity against municipal and provincial governments. Footnote 53 The Cyber Centre is aware of over 100 cases of cyber threat activity targeting Canadian municipalities since the beginning of 2020. Most cases involved social engineering, unauthorized network access or the deployment of malicious code, such as ransomware. Compromises against any level of government can implicate residents’ personal information, service continuity, and trust in the compromised institutions. Footnote 54
State-sponsored actors targeting critical infrastructure
State-sponsored actors target critical infrastructure to collect information through espionage, to pre-position in case of future hostilities and as a form of power projection and intimidation. In previous NCTAs, we assessed that state-sponsored actors were very unlikely to intentionally disrupt Canadian critical infrastructure. Over the next two years, we assess that this will very likely remain true in the absence of direct hostilities with Canada. The invasion of Ukraine has demonstrated that Russia is increasingly willing to use cyber activity against critical infrastructure as a foreign policy lever. The Cyber Centre issued cyber threat bulletins in 2022 advising of foreign cyber threat activities, including by Russian state-sponsored threat actors, targeting Canadian critical infrastructure network operations and OT. Footnote 55
State-sponsored cyber threat activity is impacting Canadians

We assess that the state-sponsored cyber programs of China, Russia, Iran, and North Korea continue to pose the greatest strategic cyber threats to Canada. State-sponsored cyber threat activity against Canada is a constant, ongoing threat that is often a subset of larger, global campaigns undertaken by these specific states. These campaigns target Canada for a variety of reasons, including our association with groups such as NATO and the G7. While state-sponsored cyber activity targets Canada directly, our high degree of global connectivity and technological integration with our allies also increases our threat exposure. Malicious cyber threat activity sponsored by states almost certainly impacts Canadian individuals and organizations, whether they are the intended targets or not.
Foreign states are targeting Canadian individuals
Targeting diaspora populations and activists in Canada
Adversary states are interested in monitoring and disrupting the activities of individuals who they believe threaten their domestic security and stability. State-sponsored cyber threat actors almost certainly target foreign nationals, diaspora groups, activists, and journalists to monitor and control these individuals. This activity likely threatens individuals’ safety and security, in addition to increasing distrust and polarization in Canadian society. We assess that threat actors are almost certainly using cyber tools against these populations in Canada. This activity takes several forms, including content monitoring on foreign-based applications, social media-enabled activity and espionage against individuals using spyware. We assess that Chinese, Iranian, and Saudi Arabian state-sponsored cyber threat actors have almost certainly monitored diaspora populations and activists abroad using a combination of these means. Footnote 56 We judge it very likely that these cyber threat actors are targeting these individuals in Canada.
According to reporting from The Citizen Lab at the University of Toronto, a research organization focusing on cyber security and human rights, cyber threat activity targets activists in Canada through disinformation or intimidation on social media, denial of service attacks against their organizations, and compromise of their personal devices. Footnote 57 Spyware tools used by cyber threat actors to compromise a personal device can be highly sophisticated, with some providing access to an individual’s personal device without requiring them to click on a malicious link or open a malicious attachment. Footnote 58
Commercial cyber tools and services on the rise
Nation states without sophisticated cyber capabilities can purchase tools and services from commercial providers. We assess that foreign governments are almost certainly leveraging commercial software, such the NSO Group’s Pegasus spyware, to monitor dissidents, activists, journalists, and diaspora groups. Foreign governments have almost certainly used these commercial tools against Canadians and groups of interest inside Canada.
Beyond cyber threat activity against individuals, states very likely use foreign-based social media and messaging applications popular with diaspora groups in Canada and around the world to monitor communications. States take advantage of permissive terms of use and their own legislative powers to compel data sharing. Footnote 59 This activity threatens the privacy of the communities using these applications.
Targeting the personal information of Canadians
In NCTA 2020, we discussed how state-sponsored cyber threat actors target large databases of personal information and use data science to identify, profile, and track individuals, likely enabling further cyber threat activity. As the amount of personal information online increases, it becomes easier for threat actors to collect and analyze information. When data is transmitted through or stored on a server physically located in a foreign state, that state can more easily compel private organizations to supply this data, threatening the privacy of Canadians. Footnote 60 The interconnected nature of communications technology and data processing means that, without appropriate safeguards, Canadians’ personal information can be compromised when cyber threat actors compromise foreign entities. Footnote 61
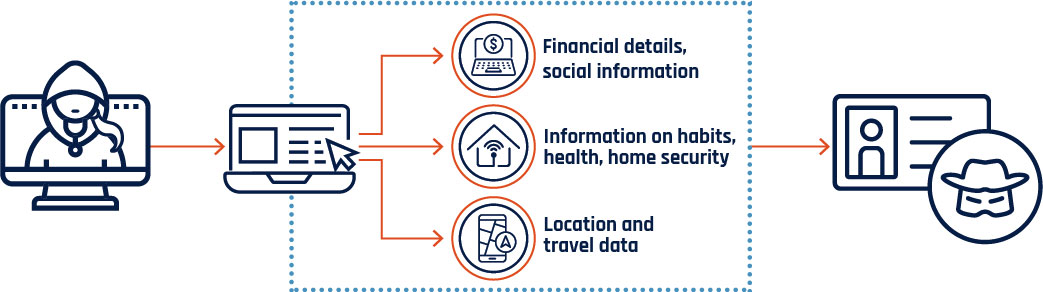
Long description - Figure 8
Graphic depicting how large datasets/personal information can be used by cyber threat actors. Online services often collect personal information from their users to function. When personal information is exposed through data breaches or willingly released by the user, it can be used by cyber threat actors to facilitate identity theft or targeted fraud against the user.
Cyber threat actors can collect financial details and social information, information on habits, health, and home security, and location and travel data.
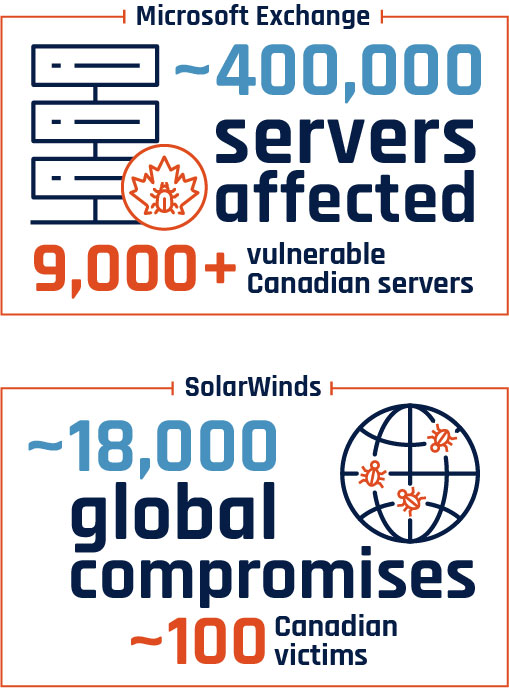
Long description - Figure 9
Graphic depicting the total number of servers affected by the Microsoft Exchange compromise and the number of Canadian servers that were vulnerable.
Graphic depicting the number of global SolarWinds compromises and the number of Canadian victims.
Microsoft Exchange: Approximately 400,000 servers affected and 9000+ vulnerable Canadian servers
SolarWinds: Approximately 18,000 global compromises and around 100 Canadian victims
State-sponsored threat actors are attempting to compromise Canadians in worldwide, widespread campaigns
Since the publication of NCTA 2020, we have observed state-sponsored threat actors exploiting commonly used software platforms to target thousands, and sometimes hundreds of thousands, of victims across the globe. We are increasingly observing state-sponsored actors taking advantage of zero-day vulnerabilities to compromise victims at scale. By targeting unreported vulnerabilities in commonly used systems, threat actors maximize their range of potential victims and prioritize those of high intelligence value for further malicious cyber threat activity. In March 2021, Chinese state-sponsored cyber threat actors compromised Microsoft Exchange servers worldwide in what was very likely an effort to steal intellectual property and acquire personal information. Globally, an estimated 400,000 servers were affected by this activity. Footnote 62 While it is difficult to determine the number of compromises, we assess that upwards of 9,000 Canadian servers were very likely vulnerable.
Software vulnerabilities and exploits
Software vulnerabilities are weaknesses or flaws in the design, implementation, operation or management of an information technology system, device, or service that provides access to cyber threat actors. Zero-day vulnerabilities are those that are unknown to the public or software vendor, and thus no patch is available. An exploit is malicious code that takes advantage of an unpatched vulnerability.
We assess that state-sponsored cyber threat actors will almost certainly continue to opportunistically exploit victims in large-scale, worldwide cyber campaigns. Even if Canadian individuals and organizations are not specifically targeted, the widespread use of common Internet technologies and software amongst our allies and worldwide means that Canadians will likely be implicated in future campaigns of this nature.
States are targeting Canada’s economic value
State-sponsored threat actors engage in commercial espionage, targeting intellectual property and other valuable business information with the goal of sharing stolen information with state-owned enterprises or domestic industry in their home country. Commercial cyber espionage is often part of a broad spectrum of activity that includes intellectual property theft, foreign intelligence operations, covert equipment and materials acquisition, and export control violations. If successful, this activity can result in lost revenue, reputational damage, and lost investment for research and development. We assess that over the next two years, Canadian organizations with information of value to foreign states will almost certainly continue to be targeted by malicious cyber threat activity from state-sponsored actors.
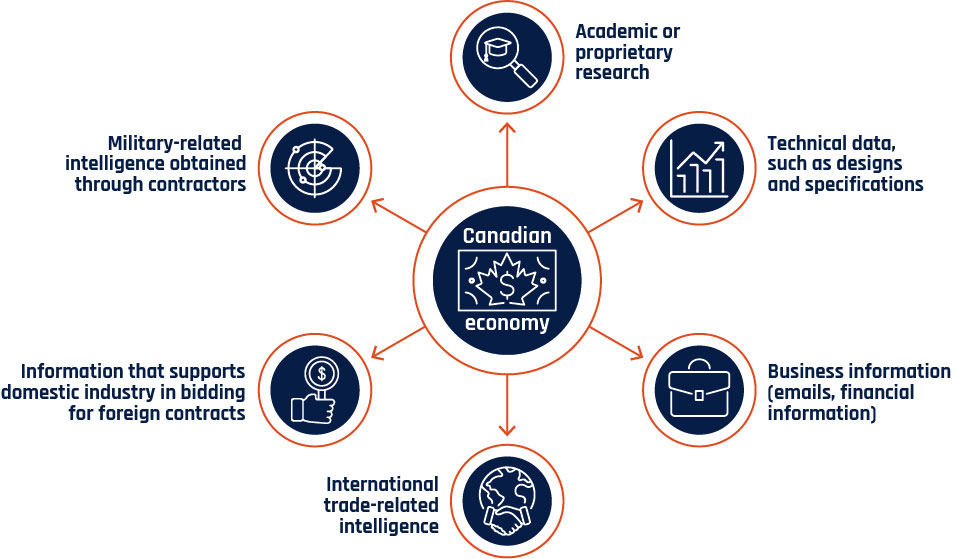
Long description - Figure 10
Graphic depicting the targets of interests for espionage relating to the Canadian economy.
- Academic or proprietary research
- Technical data, such as designs and specifications
- Business information (emails, financial information)
- International trade-related intelligence
- Information that supports domestic industry in bidding for foreign contracts
- Military-related intelligence obtained through contractors
Chinese, Russian, Iranian, and North Korean state-sponsored cyber actors each pose unique strategic threats to Canadian organizations. It is likely that over the next two years, these states will continue to target sectors of importance for their own domestic economic development. That said, the threat from China is very likely the most significant by volume, capability, and assessed intent. China-sponsored cyber threat actors will very likely continue targeting industries and technologies in Canada that contribute to the state’s strategic priorities. Footnote 64 In 2021, the US Department of Justice unsealed indictments against Chinese state-sponsored cyber threat actors who targeted science and technology research in 12 countries, including Canada, between 2011 and 2018. The industries targeted included maritime technology, vaccines and virus treatments, information technology, aviation, and defence. Footnote 65 The information stolen by threat actors was very likely intended to support China’s efforts to secure foreign contracts for its state-owned enterprises, in addition to its own research programs.
States are pursuing financial gain via cyber means
In 2021 and 2022, we observed state-sponsored cyber threat actors conducting operations for financial gain, very likely in part to alleviate the impact of international economic sanctions. States’ encroachment into financially motivated cyber threat activity increases the likelihood that Canadian individuals and organizations will be impacted by state-sponsored cyber threat activity. For example, North Korean state-sponsored cyber threat actors will almost certainly continue targeting financial institutions to generate revenue over the next two years. North Korean cyber actors have targeted individuals and organizations, including in Canada, by developing malicious cryptocurrency trading applications that can be used to capture individuals’ credentials and steal funds. Footnote 66
States are using cybercrime tools and activities to avoid attribution
State-sponsored threat actors also use cyber tools and activities associated with cybercriminals to achieve geopolitical goals, including disrupting adversaries. Ransomware has been used by state-sponsored threat actors to disrupt their victims’ operations and steal valuable business information, in addition to collecting funds from the ransom payment itself. By adopting the tactics, techniques and procedures of cybercriminals, state-sponsored cyber actors are likely attempting to avoid blame and hide their activities. For example, Iranian state-sponsored cyber threat actors have used ransomware against organizations in the Middle East and the US. Throughout late 2020 and 2021, researchers identified several Iranian cyber threat actors deploying ransomware. In many cases, these attacks are used to enable commercial espionage, while also resulting in a payout for the threat actors. Footnote 67
Cyber threat actors are attempting to influence Canadians, degrading trust in online spaces

The Internet is a crucial source of information for Canadians. Since the start of the COVID-19 pandemic, 90% of Canadians have used online sources to stay up to date with infection rates, public health measures, and vaccine development. Footnote 68 The integrity of the information Canadians receive from online sources is important. It informs their opinions and decision-making regarding public health measures and international events and influences how they engage with democratic processes. Misinformation, disinformation and malinformation (MDM, see figure 11) pollute the online information space by spreading false and potentially harmful information, making it difficult for Canadians to separate truth from falsehoods. Of the Canadians who sought information about COVID-19 online, 96% reported being exposed to content they suspected was misleading, false or inaccurate. Footnote 69
Figure 11: Definitions of misinformation, disinformation, and malinformation Footnote 70

Misinformation: False information not intended to cause harm.

Disinformation: False information intended to manipulate, cause damage, or guide people, organizations, and countries in the wrong direction.

Malinformation: Information that stems from the truth but is often exaggerated in a way that misleads and causes potential harm.
Individuals may be targeted by MDM to inflict reputational damage, or MDM may be intended to influence much larger groups. Some MDM activities are centered around an individual event, such as an election or census, while others are persistent campaigns. Social media algorithms have almost certainly contributed to the spread of MDM, and efforts by some social media platforms to moderate content have created a market for alternative, closed platforms. We have observed cyber threat actors’ use of MDM evolve over the past two years. Machine-learning enabled technologies are making fake content easier to manufacture and harder to distinguish from legitimate content. Further, nation states are increasingly willing and able to use MDM to advance their geopolitical interests. We assess that Canadians’ exposure to MDM will almost certainly increase over the next two years.
Cyber threat actors exploit technology to spread MDM and deceive Canadians
Algorithms amplify MDM
Information flows on the internet are influenced by algorithms that serve users with targeted content and advertisements likely to lead to engagement. MDM content often contains emotive and controversial content that tends to receive higher rates of user engagement. Footnote 71 As these algorithms adapt over time to account for individuals’ opinions and preferences, they can facilitate the spread of MDM by delivering to those predisposed towards believing it. Footnote 72 Cyber threat actors almost certainly exploit social media algorithms to spread their messaging. It is also likely that these actors leverage legitimate voices on social media to covertly promote their influence activities. For example, August 2021 reporting from Facebook suggests that a Russia-linked influence campaign created several fake accounts that promoted disinformation related to COVID-19 vaccinations, which was then further shared by influencers on Instagram. Footnote 73
As more mainstream platforms work to remove false content, MDM has been observed on social media platforms catering to niche audiences that provide a space for like-minded people to interact and perpetuate extreme narratives. For example, during the 2020 US presidential election, Russian actors targeted far-right American users on applications such as Gab and Parler with online foreign influence activity that promoted the incumbent, former President Donald Trump and denigrated then‑presidential candidate, Joe Biden. Footnote 74 Closed, largely unmoderated messaging applications such as Telegram are also increasingly serving as a forum for MDM content distribution. Footnote 75
Synthetic content calls all information into question
In NCTA 2020 and the 2021 update to our Cyber threats to Canada’s democratic process assessment, we described how the technology to make deepfake videos portraying public figures or events was becoming more accessible to cyber threat actors and more convincing. We have continued to observe the technology behind deepfakes evolve and witnessed its use around significant international events. When targeted at individuals, synthetic content is often intended to intimidate and inflict reputational damage on its victims. For example, deepfake technologies have been used to target politicians and journalists, primarily women, to create non-consensual pornography to silence and discredit them. Footnote 76 As deepfakes become harder to distinguish from genuine content and the tools to create convincing deepfakes become more widely available, cyber threat actors will very likely further incorporate the technology into their MDM campaigns, allowing them to increase the scope, scale, and believability of influence activities.
Deepfakes’ disproportionate impact on women
We assess almost certainly that the most immediate illicit use of deepfake technologies has been directed at women who are at a higher risk of being depicted in sexually explicit synthetic content without their consent. Some researchers estimate that 95% of all deepfake videos on the Internet contain non-consensual synthetic pornography and that about 90% of these depict women. Footnote 77 Some of the most popular deepfake tools available today are apps that “digitally undress” pictures and generate personalized deepfake pornographic material. Footnote 78
Synthetic content augments MDM campaigns by providing visual evidence backing up false claims. Text generators have progressed to a point where the content they produce is often nearly indecipherable from legitimate material. Footnote 79 Commonly available methods of deepfake video and synthetic image generation can still be flagged as fake and some are easily distinguishable from real content. However, more sophisticated examples continue to improve in quality and present challenges for detection. Footnote 80 Throughout the Russian invasion of Ukraine, we have observed synthetic content being distributed alongside a concerted disinformation campaign by Russia.
Deepfakes during Russia’s invasion of Ukraine
The Russian invasion of Ukraine has involved a sustained campaign of disinformation designed to create confusion and interfere with international perceptions of the war. On March 16, 2022, a deepfake video of Ukrainian President Zelenskyy was circulated on social platforms. The deepfake had President Zelenskyy asking Ukrainian soldiers to surrender to Russia. Footnote 81 Earlier in 2022, unknown actors posing as the mayor of Kyiv secured video calls with several European mayors. Call participants had no idea that the other caller was a deepfake until the supposed mayor of Kyiv began making suspicious comments. Footnote 82
Foreign actors use MDM to influence international narratives
We described in NCTA 2020 how online foreign influence activities have become a new normal, with adversaries seeking to influence elections and impact international discourse related to current events. This trend has continued since 2020. Adversary states constantly circulate and amplify MDM that supports their interests around significant events like the Russian invasion of Ukraine. We assess that MDM propagated by state-sponsored cyber threat actors represents an ongoing, persistent threat to Canadians. Canada’s active participation in the international community and membership in key organizations, such as NATO and the G7, almost certainly makes Canadians a target for online foreign influence campaigns.
While we assess that Canada is not a primary target for Russian MDM activities, Russia disinformation does target the West and has opportunistically seized on events implicating Canada. In April 2022, CSE reported that Russia was spreading MDM about Canadian Forces members committing war crimes in Ukraine and using fake images to back up false narratives about Canada’s involvement in the conflict. Footnote 83 In one online survey of Canadian social media users, over half of the respondents reported encountering MDM relating to the Russian invasion of Ukraine on social media. Footnote 84
Online foreign influence activity very likely also targets linguistic minorities and diaspora communities in Canada. State-sponsored cyber threat actors aim to influence these groups in order to minimize dissent or support the policies of their country of origin. Footnote 85 These groups often interact on platforms that are semi-closed and censored according to restrictive content regulations, meaning that MDM can very likely spread more easily throughout these groups. Footnote 86 For example, WeChat, a social media app from China used by billions around the world, has been used to spread MDM and propaganda specific to the Chinese diaspora. Footnote 87
Disruptive technologies bring new opportunities and new threats

The rapid development of technology has created many opportunities for those successful in creating, scaling, and deploying innovations. Some developments can be said to be “disruptive” because they fundamentally alter their area of application, providing significant improvements over existing technologies or new approaches that make incumbent technologies obsolete. However, regulation often struggles to keep up with leading-edge technological development, and the implications and risks of adoption are not always initially clear.
Just as advanced technologies can be used to support commercial and public objectives, they can be maliciously deployed by sophisticated threat actors. This section discusses three of the technological trends we assess as having the potential to disrupt their respective fields: digital assets and decentralized finance, machine learning, and quantum computing. While these technologies are in varying states of development and realization, they all have implications for Canada’s economic prosperity, national security, and the individual safety and privacy of Canadians.
Digital assets are targets and tools for cyber threat actors
Since Bitcoin debuted as the first cryptocurrency in 2008, the number of cryptocurrencies and the value of cryptocurrency markets has exploded. There are now over 10,000 different cryptocurrencies being traded. The market cap peaked at almost $3 trillion USD during the COVID-19 pandemic before dipping just below $1 trillion in mid-2022, still well above pre-COVID-19 levels. Footnote 88 Cryptocurrencies and their supporting blockchain technologies have contributed to the development of a digital-based economic ecosystem, where digital assets have real-world value. An emerging aspect of this system is Decentralized Finance, often referred to as DeFi, which allows large-scale borrowing and lending of funds without intermediaries. These activities occur on DeFi platforms that provide a broad range of services and serve as an alternative to traditional, centralized financial systems based on banks and similar institutions.
According to vendor analysis, cryptocurrency theft peaked in 2021 to almost $3.2 billion in value from both cryptocurrency exchanges and DeFi platforms. Footnote 89 In addition to stealing cryptocurrency through fraud, scams, and digital wallet compromise, cyber threat actors rely on cryptocurrency to pay for illicit goods and services, to receive payments from ransomware victims, and to launder criminal proceeds. While law enforcement has had some success in tracking and, in some cases, recovering stolen funds, cyber threat actors continue to refine and develop techniques for obscuring illicit financial transactions, such as the use of mixers or privacy coins. Footnote 90 We assess that cryptocurrency money laundering will almost certainly continue to facilitate the growth of cybercrime and other illicit activities and impede law enforcement’s ability to track and recover funds.
Figure 12: Cryptocurrency terms

Privacy coins
Cryptocurrencies such as Bitcoin operate on a public blockchain, meaning that all transfers and transactions are public. Privacy coins such as Monero are specifically designed to obscure transactions and ensure the anonymity of users. This makes privacy coins attractive for cyber threat actors who have an inherent interest in avoiding detection and making it difficult for law enforcement to follow illicit money flows. Footnote 91

Mixers
Mixers allow cyber threat actors to obfuscate the origin of illicitly obtained cryptocurrency. Mixers accept cryptocurrencies from users and combine them into a collective pool, effectively “mixing” them together. Users then withdraw the value of their deposit from the mixed pool, minus a service fee. Mixers have seen increased use, breaking $1 billion USD in quarterly value received at the end of 2020 and ranging from $2 billion to just over $3 billion USD every quarter since. The increase has been driven by funds received from suspected illicit sources, which in the second quarter of 2022 accounted for around 28%, or $700 million USD, of value sent to mixers. Footnote 92
Machine learning automations can be deceived and exploited
Machine learning is a rapidly developing subset of artificial intelligence that has already become commonplace in consumer services and data analysis. Machine learning techniques present a fundamental shift in the automation of tasks such as image recognition, language translation, and online content moderation or curation. Researchers have demonstrated many other promising applications for machine learning in the future, including for self-driving vehicles and medical diagnostics. Footnote 93 As machine learning is incorporated into decision-making processes with significant societal or personal impacts, care will need to be taken to ensure its application is equitable, unbiased, and secure. Machine learning applications have unique vulnerabilities compared to traditional programming. These can be exploited by cyber threat actors, adding to the threat surface of the organizations that employ them.
Cyber threat actors attack machine learning models through adversarial machine learning techniques. Footnote 94 Broadly, these techniques exploit flaws in the machine learning model’s logic to deceive it or force it to return unintended, sometimes confidential, information.
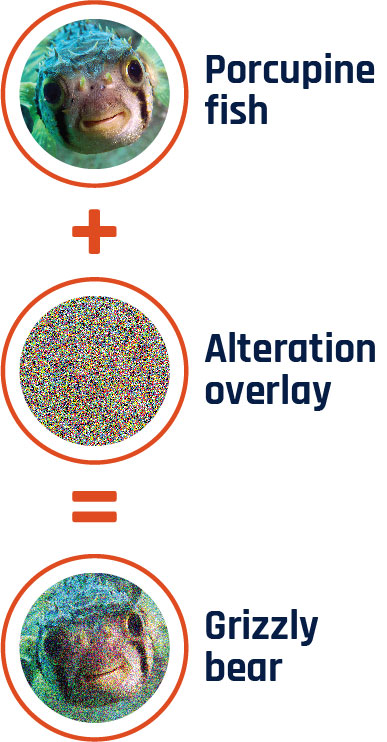
Long description - Figure 13
Graphic depicting how an image recognition machine learning model can be deceived by subtly altering the image. A picture of a porcupine fish is combined with an alteration overlay. The altered porcupine fish image looks nearly the same to humans, but the image recognition model instead now perceives it as a grizzly bear.
As illustrated in Figure 13, image recognition machine learning models can be tricked into misidentifying objects by subtly altering the image. Some alterations are invisible to the human eye, making them difficult to detect. Footnote 95 The same principle applies to other machine learning applications, such as malware detection. By subtly altering the code of the malware in ways that confuse the algorithm, cyber threat actors may trick security software into misclassifying malware as benign. We assess that cyber threat actors are also very likely deceiving machine learning algorithms to enable their other threat activity, such as the distribution of misinformation and large-scale email fraud campaigns. Footnote 96
By providing the machine learning model with carefully crafted queries, cyber threat actors may be able to infer information from the training data. Footnote 97 Where the machine learning model is applied to medical diagnosis or fraud protection, the training data may include sensitive personal information, including health history or financial details. Exposure of that information, or that an individual was part of the training data, can be used for further tailored threat activity like fraud and scams. Personal information stolen in this way is at risk of further exposure should it be sold or released publicly.
Quantum computing threatens modern cryptography
Quantum computing is an emerging technology intended to overcome the physical limitations of conventional computing through the application of quantum physics. Quantum computers threaten our current methods for ensuring the cyber security of information systems and protecting sensitive data transmitted over the Internet. Cryptography is used to protect data using mathematical problems that certify the source and scramble its contents from unintended viewers. Without the decryption key, breaking the security by solving the mathematical problem could not be done in a reasonable timeframe with classical computers. However, the mathematical problems underpinning current cryptographic standards are easily completed by quantum computers. Quantum devices powerful enough to break modern cryptography could be available as early as the 2030s, making it impossible to securely transmit sensitive information if changes to our current cryptographic methods are not made. Footnote 98 However, we have yet to observe quantum computers capable of completing problems providing commercial advantage that could not also be completed by classical computers. Footnote 99
Cryptography is essential for common digital systems of trust that require transfers of sensitive data, such as personal details or financial information. We assess that the proactive development and adoption of quantum-resistant cryptography will likely diminish the threat to future information and communications should quantum computing become more capable and common. The Cyber Centre has been active in developing a solution to the quantum challenge, working with the US National Institute of Standards and Technology to certify standards for quantum-resistant cryptography. Footnote 100 However, encrypted information stolen by threat actors today can be held and decrypted when quantum computers become available. For most Canadians this may not be a significant threat; however, stolen commercial information and government data related to foreign affairs or national security may still be valuable or sensitive in the future. Footnote 101
Conclusion
The cyber threat landscape in Canada continues to evolve. Canadians use the Internet more often and for a greater number of tasks. As more devices are connected to the Internet, the cyber threat surface expands. Cyber threat actors adapt their activities and utilize new technologies to achieve their financial, geopolitical, or ideological goals.
In this National Cyber Threat Assessment, we identified trends within the threat landscape and provided an overview of five themes that we anticipate will drive cyber threats to Canada over the next two years. While cybercrime remains the threat most likely to affect Canadians and Canadian organizations, state-sponsored cyber threat activity is also impacting Canadians. Critical infrastructure is increasingly at risk from cyber threat activity from both cybercriminals and state-sponsored actors, while nation states are evolving their use of misinformation, disinformation, and malinformation to influence Canadians. The cyber threat landscape will almost certainly evolve further over the next two years as technologies such as digital assets, machine learning, and quantum computing bring new opportunities and new threats.
Many cyber threats can be mitigated through awareness and best practices in cyber security and business continuity. Cyber threats and influence operations continue to succeed today because they exploit deeply rooted human behaviours and social patterns, not merely technological vulnerabilities. Defending Canada against cyber threats and related influence operations requires addressing both the technical and social elements of cyber threat activity. Cyber security investments will allow Canadians to benefit from new technologies while ensuring that we do not unduly risk our safety, privacy, economic prosperity, and national security.
The Cyber Centre is dedicated to advancing cyber security and increasing the confidence of Canadians in the systems they rely on daily, offering support to critical infrastructure networks as well as other systems of importance to Canada. We encourage readers to consult our cyber security guidance for more information on the cyber threats and trends outlined in this document.
At the Cyber Centre, we approach security through collaboration, combining expertise from government, industry, and academia. Working together, we can increase Canada’s resilience against cyber threats.